New on the scene: DarkVision RAT
Recently, Deep Instinct’s Threat Research Team has identified a new and emerging, highly modular, malicious RAT entitled DarkVision RAT, which during our investigation we found is also being actively sold in a well-known cybercrime and hacking-related forum and also a dedicated sales website.
A relatively new member to the threat landscape, and possessing a wide range of plug-ins and various functionalities, including password harvesting, OS message prompts, encrypt/decrypt ability, DarkVision is capable of facilitating a wide array of malicious activities such as spying, fraud and even ransomware-like activities, to name just a few. However, for many, its emergence and proliferation among dwellers of “underground” forums is more interesting than what it can actually do. DarkVision is getting around in no small part by the business savvy of its creator and developer. Neatly packaged into a kit, the RAT is “attractively” priced at $40 USD and marketed for its nice set of features, cost-effectiveness, and quick deployment which can only take minutes to put into action. Just new on the scene, the RAT’s creator continues to make sales and improve his offering to meet market demand.
DarkVision's Offering
RATs (Remote Access Tools/Trojans) are a staple in the threat landscape, commonly used by malicious actors to gain and provide remote access to and monitoring of infected machines and to facilitate a host of malicious activities.
DarkVision RAT made its first “commercial offering” in mid-January, described as a "Remote Access Tool (RAT) for Windows 7/8/10 (32/64 bit) with a native core written in C++ and ASM, which makes it standalone and free from any third party dependencies (like .NET).”
The DarkVision RAT is offered as a simple, easy to use and user-friendly kit employing a modular plug-in architecture; It is described as a long-term project which includes “lifetime support” and free/discounted upgrades to future versions upon request. In addition to the forum offering, DarkVision’s author has also established a website intended to market the RAT.
Figure 1: DarkVision Forum Offering

Figure 2: DarkVision Website Offering
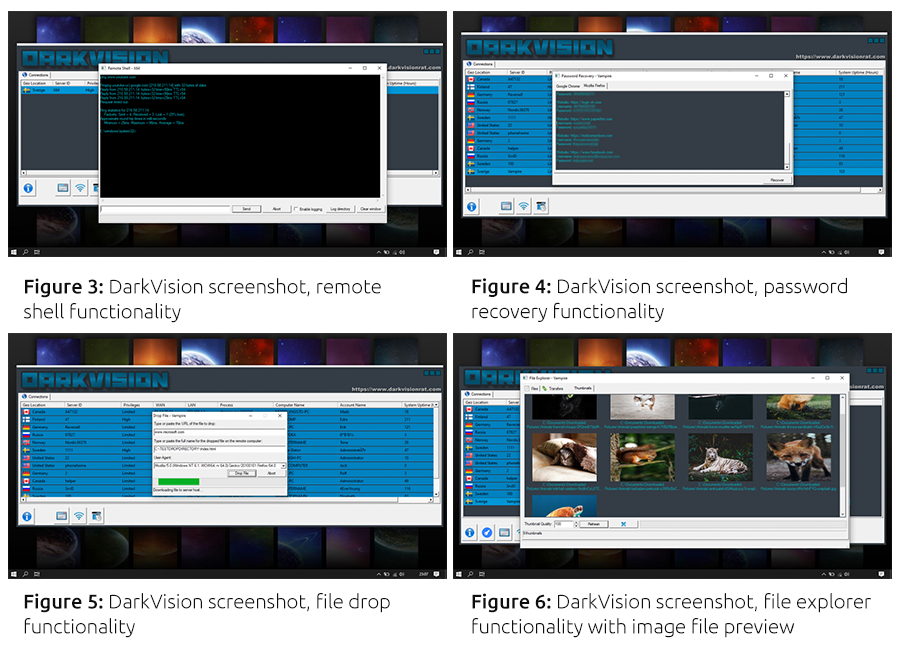
Screenshots and videos of various functionalities are also provided on both forum on website:
Shortly after its appearance on the forum, DarkVision started receiving positive feedback:
Figure 7: Forum user vouching for DarkVision
Figure 8: Forum user vouching for DarkVision
Following a short period of inactivity by the author, a user wondered if the author had been arrested by law enforcement:

Figure 9: Forum user wondering if the author has been "raided"
To which the author replied:
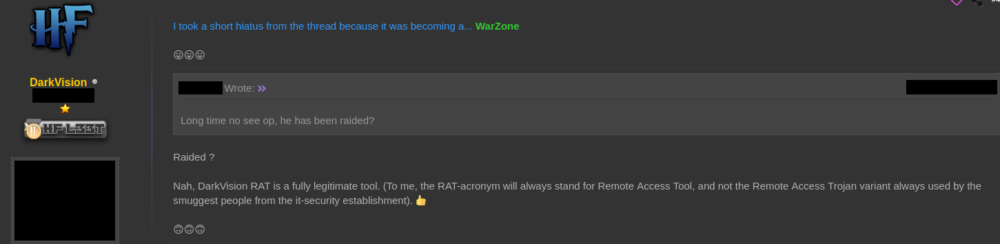
Figure 10: Author's response
The author also appears to be very responsive to requests and feedback, adding new features and functionality, such as an encrypter (a method to encrypt the payload in order to avoid its detection by security products) and hidden VNC/RDP functionality:
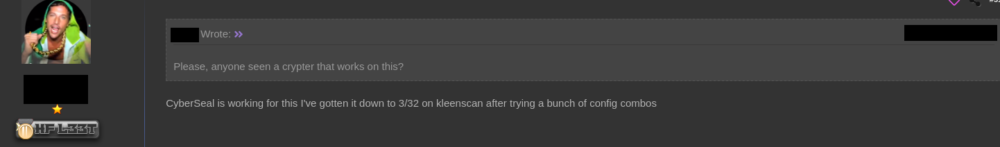
Figure 11: Forum users discussing possible encrypters for DarkVision
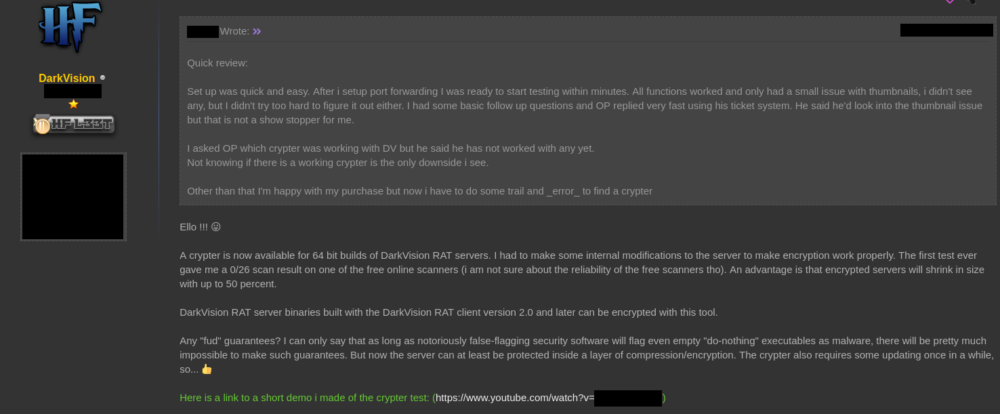
Figure 12: Author announcing DarkVision encrypter
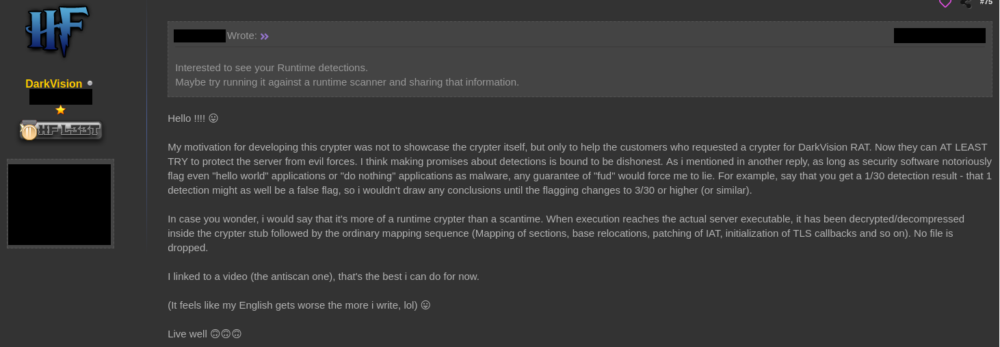
Figure 13: Author explaining his motivation for creating the encrypter
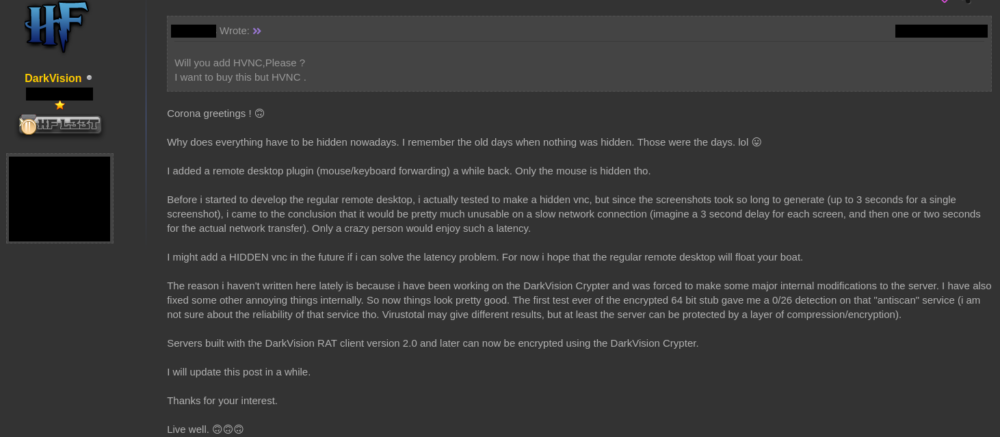
Figure 14: Author discussing additional hidden VNC and RDP functionality
Hands-On with DarkVision
In addition to encountered samples of DarkVision (listed in IOC section below), Deep Instinct’s Threat Research Team managed to identify an operational security failure by either DarkVision’s author or one of his customers and get our hands on a version of the DarkVision kit.
While lacking the author’s latest developments (namely the RDP plugin and payload encrypter), the kit proved very interesting to analyze.
Our recovered kit contained an executable file that functions as both the RAT payload builder and control interface with its infected machines a set of 17 plugins .DLL files (32 and 64-bit version of each), each responsible for different functionalities. These plugins can be selectively delivered to the infected machines based on desired functionalities and are loaded by the RAT directly into memory, without being written to disk (with the exception of the Chat plugin).
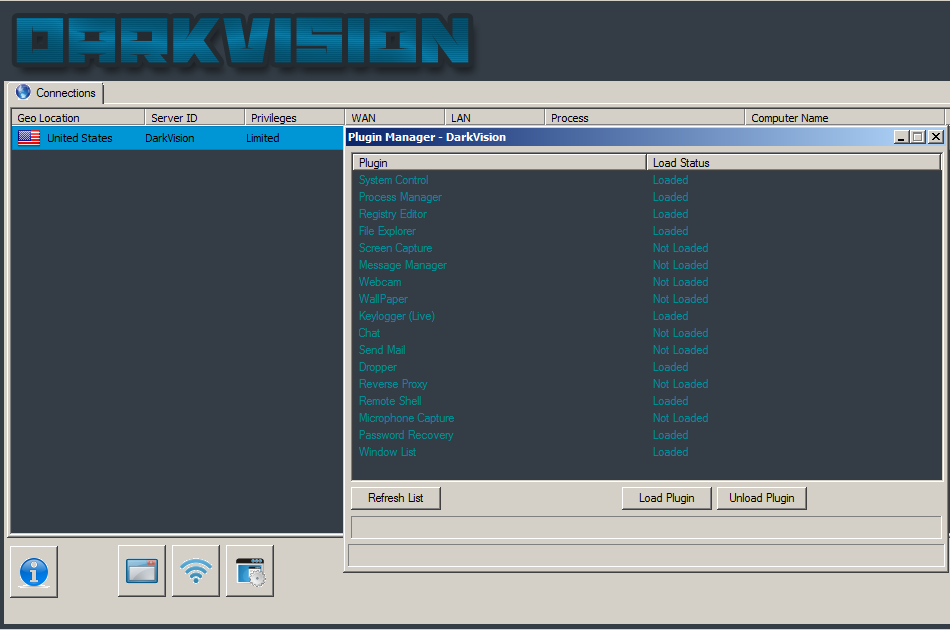
Figure 15: DarkVision plugin manager
Plugin Functionalities:
- System Control – Lock, reboot, or shutdown victim machine.
- Process Manager – List active processes, kill selected.
- Registry Editor – Edit victim machine' registry.
- File Explorer – File manager-like utility, manipulate files (copy, delete, move, etc.) on the victim machine, upload file to or download file from victim machine, view image previews/thumbnails, execute files, encrypt/decrypt files with AES 256 and the desired password (encrypted files are appended with a “.DVCRYPT” suffix and file headers replaced to “DVCR”). This type of functionality usually lies in the realm of ransomware.
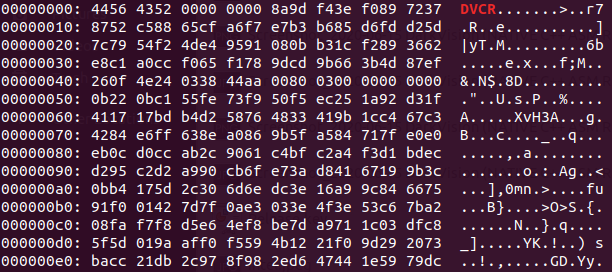
Figure 16: Executable file encrypted by DarkVision
- Screen Capture – Capture victim user’s screen in intervals of up to 10 seconds. When this interval is set to 0 the victim’s screen is effectively “streamed” to the attacker.
- Message manager – Display a customizable operating system prompt and return the response (if the user clicked “OK” or “Cancel”, etc.).
- Webcam – Capture webcam video.
- Wallpaper – change the victim machine’s windows wallpaper.
- Keylogger (Live) – Logs and displays victim user’s current keystrokes and to which window they were made.
- Chat – Opens a chat window with the victim user.
- Send Mail – Send an Email from the infected machine.
- Dropper – Download a file from the internet to a desired location on the infected machine.
- Reverse Proxy – SOCKS4 Proxy functionality.
- Remote Shell – Remote CLI Shell to the infected machine, execute commands, etc.
- Microphone capture – Capture microphone audio.
- Password Recovery – Chrome and Firefox stored password harvester.
- Window List – List currently open operating system windows.
DarkVision refers to its payloads and infected machines as “servers”, possibly in order to avoid calling them “bots”, and possibly due to the fact that they have some server-like functionalities.
Conclusion
Although new to the scene and lacking several functionalities found in other such malicious tools (such as cookie harvesting and hidden VNC, both features which were requested from the author…), DarkVision appears to be gaining some popularity as an overall nicely featured, cost-effective (the kit is currently priced at $40) and very easy to use malicious RAT; capable of facilitating a wide array of malicious activities such as spying, fraud and even ransomware-like activities, to name just a few.
DarkVision is in active development and will likely continue to evolve and add additional features, functionalities, and abilities, its emergence offers an interesting glimpse into the emergence and proliferation of such tools.
DarkVision’s author is presumed to be a Swedish-speaking individual, as he is seen using a Swedish-language operating system in his demo videos, as well as operating from Swedish IP addresses.
Deep Instinct prevents DarkVision both statically (pre-execution) and dynamically with our behavioral analytics.
IOCs
DarkVision Samples (sha256)
0de5f042eb250092454d786b6303dee434202d45dc3fec9e6b39237f9e92514f
0fa8acdb672f0e6c184fc5d04bb8af92c0bf5db73de096606f23f4c38ef3347b
10667e9d67706397f7ff96e892d3c0f0ae05d81df5bc17caf85fb356d531c0b8
1a230bb362cde9ead2d9f867af181ae51292c626a3c9d1d30f5f3751b84ffe85
201f31c84755a5cd6081c3db30626cc3f17cf84804c2deb66e27866daad259a3
3295199ba2b4e9cfc448a574cb9e89f3ef131fd19dcf366fe2abb7b3b79eb887
40d48f5e965a250ac45f2f9c9426743c66fe899f07e16c42339149e30b1956e9
44de5a248b6e9c24ad547e73c3ba3c8cc9693ba6eaa5190be9b377845844ffb6
47070e4f6545f9f1308a5aec1e6943e6a29891bce9523db5596544a52f9b3bf4
478cf5482905fa2ac2a2280a03ad6716f153c372c15cd957a23a67ff3260c867
5174ef9f7d5420ab4890173792d8aafc50b8bb3191b4c24f6f58ae73bd7212c3
5cce814cadb4fac6631ff3c988516b4c6618f0c71c7de3588fc0d7038c220f31
7f97ba9a8e6b70708a001cff8677992fc1e768a62f9f21ddd14fb1c6924281bc
808680e6761782a7817fd8e3f90463738d17216b3bca51f3ca4e7375458cba1b
a3bd7d3e7006439d1d53cf8db1f403df2162c8f7e8172d6911be203ea58a2d8d
b75354d8ad3f4e0f675ec6a64c82226d75116535198ef4974b17984ccebab63e
bf1c8cf3ab6213c250d1abf8094180fdcf8e871674482fce1930abe9826e61b9
cb06287e314bf4c684323c7925922cce2932a9e9e9b6aac34634487ac7741afd
e91586b66e6d05e3b118991b72896d37c3e625e4f54ceb4ad6b04f047a31593b
eafa30bac261cc682556812c7c513827f09ef75fc33dbeb61e5d3ff46c9f3808
ee1b2b016b56950986db7b08f451220b91f1d91a70fec0624e289e96c648cb44
f36626f1a71c68c4647347b25eb0000c0e6c5d7700cf16047a3d9967321cf14b
f3b00f34857586056178a56517e4c07effe1182604b11665fb8efb71be78cec4
DarkVision Kit (sha256)
52e66bc19323536314fce12a2a3fa064b726bb71704a0d9f899d49892f265274 - dv_kit.zip # DarkVision Kit
ba59847f9f160987ee5d9ad57d5022895cece9bd4627d90f5eab35c2f29596ea - DARKVISIONENCRYPTED.EXE # Builder/control panel
447ccb93bcbc969e08ec726e1461c386668720d79d091bca889b5b5a129a352d - CHATPLUGIN32.DLL
7e1aa75831ab42fb27bd372c84e70816cee68e63c59ab66ad445e123cb4dad40 - CHATPLUGIN64.DLL
054f55d77f0250760ab3a12e63af89ba5958468215e18b522cd618363da938a1 - DROPPERPLUGIN32.DLL
83358d06da03686a452f03045219f8286d46ada3287b3a354229ae82dcbd3266 - DROPPERPLUGIN64.DLL
17ab5394041bf8230f816ea92638ec5e5515112132a8e649d4caa783d886cfdf - FILEPLUGIN32.DLL
7c43ad507d71361001464838d5a55a4753a4c8c0e9647de37e721a2d86fb5a86 - FILEPLUGIN64.DLL
3ec311c131d15a530dac35108f167ee926ef87e6cef618c6ba05d9eb239a4940 - LIVEKEYLOGGERPLUGIN32.DLL
0a3bdfe88cf7c38294a1ff2a497f3bcedb3feb8dc37fa0de7332865c348b7eb0 - LIVEKEYLOGGERPLUGIN64.DLL
a1396856c94b92cc78e9636b37ed3e998443699d6bb9f35e086bc87a5ccd0f67 - MESSAGEPLUGIN32.DLL
32eda28241805e739ecdf205f056948cd4bc0d421ccfb70e77d1027d94504587 - MESSAGEPLUGIN64.DLL
4a30c6c89f0d95bc647da438bb4783853167f997221b3ff91bda6816d4043c5a - MICROPHONECAPTUREPLUGIN32.DLL
8284d1613e68ccfd1f07b80161e38f9a96cf26f1229cd297ea1bd95809459bdd - MICROPHONECAPTUREPLUGIN64.DLL
24c3d64db7c499c6c60ae6bf406e25d6a70902cb7f2393b81555e3241aa7c43c - PASSWORDRECOVERYPLUGIN32.DLL
d9f5fe4cd4885a31c288e89447db5d77e846db5b714bb6c1a32e8692e9dd6acd - PASSWORDRECOVERYPLUGIN64.DLL
5a882cb5120fc2720df4c26a02feafcac4246c7937c7dcb6046a1f185e39a2eb - PROCESSPLUGIN32.DLL
230f27eb5652c0a169740a44375221bcda1fae8c3703e354bb756189fa0b8a07 - PROCESSPLUGIN64.DLL
b0faa36c459996787f5aadb327003497444c375e25d0e6a07bc7264608f6b18a - REGISTRYPLUGIN32.DLL
434733d083f2648719bc02e7c8b0bf300007619f20876cb9161e88f5a13d47f2 - REGISTRYPLUGIN64.DLL
7c7264939bd4e249e559f507027c1b1eb92541803e29434238165423c664fa8a - REMOTESHELLPLUGIN32.DLL
572a2d0e60147163deb9bbada3ddd7fe414096fc1b14f51bd6d17a0fc34e7131 - REMOTESHELLPLUGIN64.DLL
531ed45fca9530ae8d1b56b40b784c8d238bf739ea1c7d5779a7dc155248f47b - SCREENCAPTUREPLUGIN32.DLL
ea97e8b77b654598a46a12f6f80ace614cd0cc0b6e2060e81ca2c76ec1f9e2e8 - SCREENCAPTUREPLUGIN64.DLL
b55075d58564ce37324e5f4c746839e35293ac60fed35f345163b77944b0ed8d - SENDMAILPLUGIN32.DLL
23a2e7637acc101bf40ddc953152d7302342e3ca480353a84f6fee5e23155519 - SENDMAILPLUGIN64.DLL
9f2bb6a03ce289a2b6b10950df6ccf80ef3f25dfc2a8c0c9fa5efb3b76e1c167 - SOCKSRELAYPLUGIN32.DLL
1868425310156eafad6074aab9b3bff4c681615a03914f7b970d9e7bc476bbb0 - SOCKSRELAYPLUGIN64.DLL
99e316f57528b47af726ff2cd9a33f6c950c4c7f6b88174d491510eb44047132 - SYSTEMCONTROLPLUGIN32.DLL
39d798c7b1fa8a57dba656682d2c91beb946e10c277ad12e2b08a7b7c1d88a8c - SYSTEMCONTROLPLUGIN64.DLL
b1d5be14b2011f0628dcdd686183f2a2363febdac7e14f23eb51ffd7238b9ba2 - WALLPAPERPLUGIN32.DLL
ed6338943d6237d422e4c54ad3e33040140de6800717831c071de1a37fdf1fe9 - WALLPAPERPLUGIN64.DLL
9ad437d76f08dcb1ce86da07de067735d5b9c657c91ffb13972addce1d50cade - WEBCAMPLUGIN32.DLL
eb12c86b21b337b64f99ad7f7375bc4bbb05a7ba6b5af605ace55546af9db222 - WEBCAMPLUGIN64.DLL
96b4836f4e0e5293833e30db86660e5e45268f4a2072fbbeea8003b684756d45 - WINDOWPLUGIN32.DLL
81a857d256dbd90322fa437e8045e2e2173fce46ef05cf83df9b8fe8f62bf74c - WINDOWPLUGIN64.DLL
Network IOC
asdhuaudjwaj.kro.kr:5678
rwrw.ddns.net:1984
sharkzilla06.ddns.net:5552
83.253.89.225:5555 # Swedish IP
193.150.242.255:5555 # Swedish IP
45.153.240.147:8787
185.244.30.38:5510






