Attackers Abuse the COVID-19 Pandemic to Spread Malware
Cyber-attackers don’t let good opportunities for attack go to waste, and the Coronavirus pandemic is no exception. Attackers are using the pandemic to generate massive amounts of mal-spam and phishing, to increase their chances of infecting targets. In fact, this might be the first case in which biological viruses help spread computer viruses.
In the past few weeks, dozens of malware campaigns have started using COVID-19 themed mal-spam and phishing emails. This blog post will outline some of the campaigns that are involved, and how users and organizations can protect themselves from these, and other campaigns.
Prominent COVID-19 themed campaigns
Some of the most prominent malware campaigns of 2019 have kept apace in 2020, and are adjusting their strategies to take advantage of current events.
For example, Trickbot, the sophisticated financial malware, used fake emails from the WHO in order to lure victims into downloading a Word document attached to the email. Once the document is downloaded it then executes VBA macros and downloads Trickbot. Unsurprisingly, Emotet malware also uses the Coronavirus to spread, through phishing emails and also through a different approach, adding strings related to the Coronavirus pandemic into its executable payloads. One such example included strings from a CNN article, placed inside an Emotet executable payload and in the details section of the payload, in order to fool unsuspecting users, and possibly evade detection by security products.
In addition to high-profile cybercriminal malware, nation-state actors have also started using emails discussing COVID-19 in order to infect their targets. For example, the Russian-attributed group APT28 started using COVID-19 themed documents as bait against their targets, located in Ukraine. Other attack groups from China and North Korea have been found to use similar techniques.
A very original manipulation of the situation used a legitimate coronavirus live heat-map to spread malware. In this attempt, which might be an effort to spread the Azorult password stealer, a real JAR based Coronavirus live map is downloaded. However, the JAR file includes a malicious loader in addition to the map, which can download payloads according to the choice of the attacker.
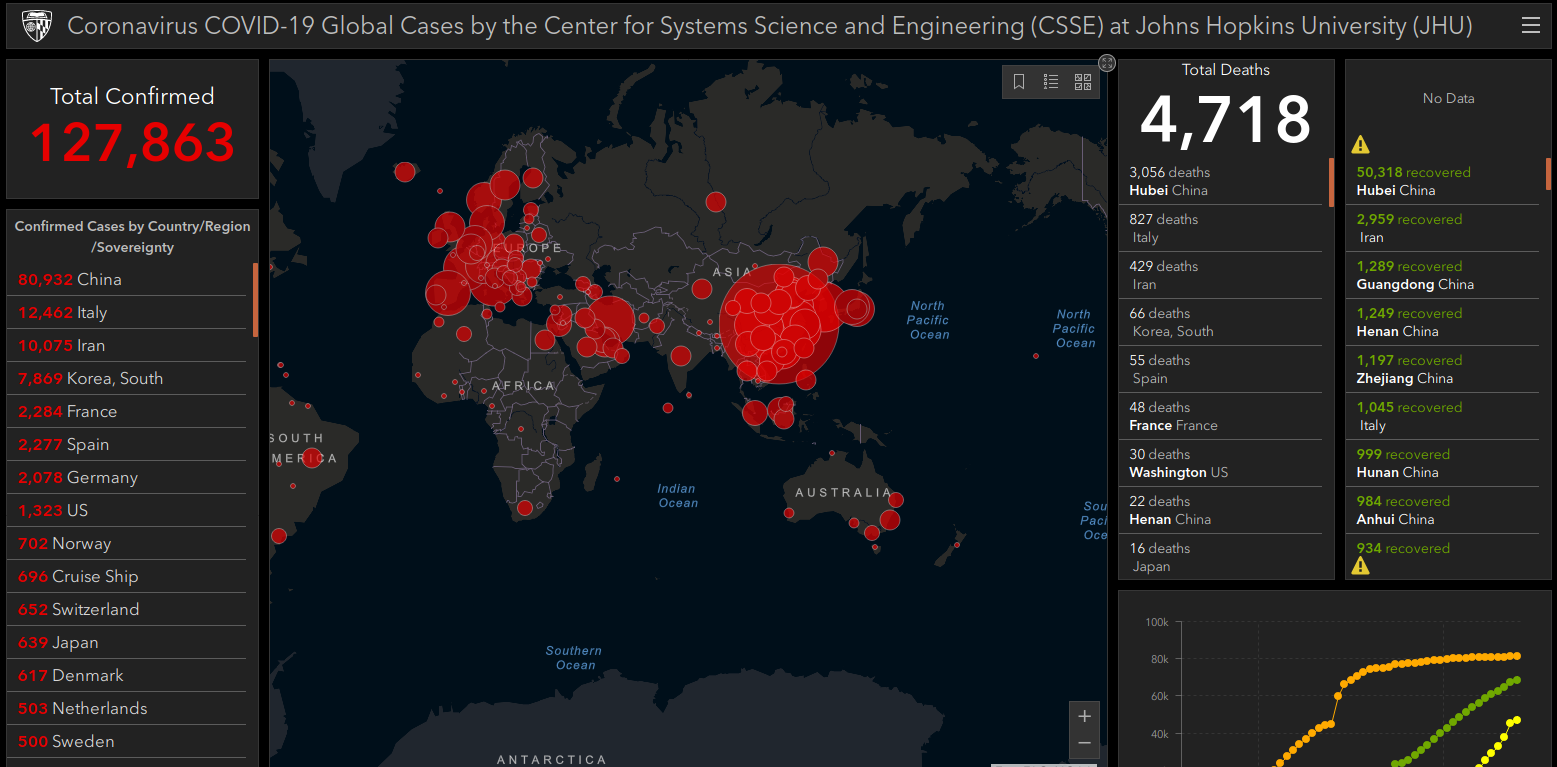
A recent snapshot of the Johns Hopkins Coronavirus data map, available at coronavirus.jhu.edu.
These are only partial examples of the way attackers are manipulating the current situation in order to spread malware.
How to protect yourself
Users and organizations can protect themselves from these threats in several different ways.
- First of all, as many phishing emails pose as emails from the WHO, it should be noted that WHO communications only come from @who.int email addresses. In addition, the WHO website has a link in which scams can be reported: https://www.who.int/about/report_scam/en/.
- Do not open emails from unknown senders. Moreover, do not open attachments from unknown or untrusted senders. Advice regarding best practice in the COVID-19 pandemic should be taken from the web-pages of official organizations, such as the WHO or your nation’s government ministries.
- Make sure you work from home safely. Tips and security guidelines are provided on this subject.
- Make sure the endpoints solutions you are using are installed with an advanced security solution that prevents malware no matter where you are, be it work or home.
Deep Instinct’s deep learning technology is able to prevent both known and unknown malware. Specifically, Deep Instinct protects against all malware campaigns mentioned in this article and is the only cybersecurity company that can prevent known and unknown JAR malware pre-execution, using our deep learning brain.






