5 Advantages of Deep Learning in Cybersecurity
When it comes to minimizing risk, organizations have been turning to AI-based solutions to detect and respond to attacks because humans cannot keep up with their variety, volume, and velocity. The majority of AI-based cybersecurity solutions feature some form of machine learning (ML). Yet, we continue to experience far too many breaches. There is an opportunity for a transformational change to adopt superior threat prevention, brought about by the most advanced form of AI – deep learning (DL).
But what is deep learning, and why should you care?
There are significant differences between ML vs DL – and when applied to cybersecurity, it’s critically important to understand the outcomes each can achieve and the key benefits of each approach.
Deep Instinct’s most recent eBook delves into these differences: How do DL and ML solutions truly compare and which is superior for advanced threat prevention?
The evolution of machine learning in cybersecurity
There are essentially three types of AI that are used in cybersecurity: Basic, Reactive, and Proactive.
As the story goes, traditional AV and NGAV were failing to prevent attacks. These solutions adopted basic AI to improve prevention, but still relied on signatures and rules to stop known attacks. By time the rules are updated, the attackers have long since modified the attack and changed tactics. In the innovation race between threat actors and cybersecurity vendors, the vendors have been a distant second for some time.
Around 2010, it was determined that ‘assume breach’ was the most logical mindset to react to cybercriminals. If it was not possible to keep the bad guys out, planning for the inevitable breach was the appropriate defense. They are going to find a way inside your environment, and solutions were built to look for behaviors of compromise and known attack techniques, employing a reactive form of AI called machine learning. Rather than stop attackers at the gates, the decision was made to assume they would break through defenses and the best plan was to deal with the aftermath post-attack.
While ML was a perceived step forward in the evolution of cybersecurity, we have now come to a point where it is not enough. More attacks are succeeding and increasingly evading the security controls, like EDR, meant to stop them. The investments made in cyber solutions that do not stop cybercriminals in addition to the post-attack costs are no longer tenable.
This is evidenced in a recent article, "EDR evasion is well-documented, but more as a craft than a science," by Karsten Nohl, chief scientist at Berlin-based SRLabs. Nohl observed, "What's new is the insight that combining several well-known techniques yields malware that evades all EDRs that we tested. This allows the hacker to streamline their EDR evasion efforts."
5 ways deep learning is transforming cybersecurity
Deep Learning holds the greatest promise to proactively prevent threats before attackers can get inside and establish a foothold. While some aspects of ML- and DL-based cybersecurity platforms may appear similar, the significant differences lie in the outcomes.
For a more in-depth explanation of ML vs DL, read the eBook.
- Prevention, pre-execution
A DL-based solution can provide instantaneous prevention of ransomware, zero-days, and other unknown attacks before a file executes and lands on the operating system – meaning it never gets the chance to detonate. Deep Learning makes it possible to prevent a threat in <20ms, before it can write to disk, virtually eliminating the threat actors ability to evade controls. - Reduction in false positive rate to <0.1%
With an industry low false positive rate, DL-based solutions deliver far fewer alerts overall, which alleviates the burden on the SOC team so that they can focus on the most pressing issues impacting the business. - Autonomous, accurate decisions without the cloud
A DL ‘brain’ is trained on all available raw data to understand the DNA of an attack. This enables a DL-based cybersecurity solution to make malicious vs benign decisions autonomously without the need to call to the cloud for intelligence feeds. - Lower resource requirements and less maintenance
DL-based solutions consume far less memory and lowers CPU consumption even with the speed and scale with which it can make decisions. The ‘brain’ can prevent never-before-seen threats without constant tuning and only requires 2-3 updates per year. - Immense scalability
Because of its autonomy, speed, and lightweight footprint, a DL-based solution is able to scale to scan tens of millions of files in milliseconds while still maintaining an extremely low false positive rate.
Machine learning vs deep learning: Under the hood
On the surface it’s all AI, so how is Deep Learning really different? Much of it has to do with the data the models can train on and how much human bias can be eliminated.
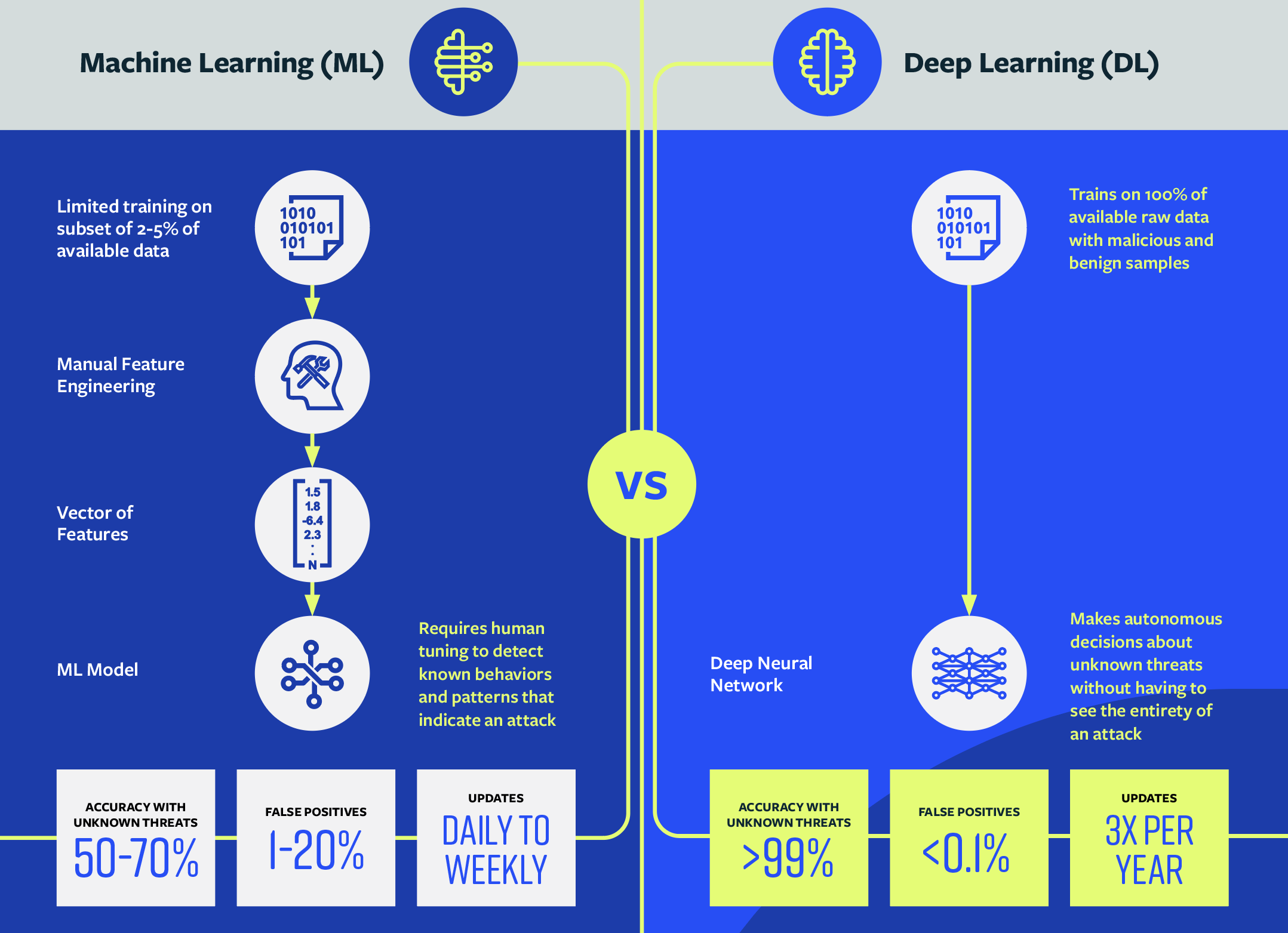
Defense-in-depth with deep learning
ML was once the most efficient, cutting-edge AI available — but we have come to realize that it’s too reactive. ML-based solutions, like EDR, are needed for investigation, correlation, and response, but we can vastly improve the outcomes and efficiency of the SOC by incorporating a prevention-first approach in the security stack. A DL-based solution can prevent malicious files uploaded by customers, third-party partners and end users, or downloaded from the internet, by scanning them before they reach the endpoint, server, or storage with zero impact on business operations.
To learn more about the differences between ML and DL solutions, and to understand how Deep Instinct can help protect your organization from the world’s most advanced threats, read our eBook: Deep Learning vs. Machine Learning in Cybersecurity; Which is Superior for Advanced Threat Prevention?
If you’d like to learn more about our deep learning capabilities, including our industry-best $3M no-ransomware guarantee, we’d be delighted to give you a demo.





