How Companies are Successfully Bringing Down the Cost of a Data Breach
There is a contentious relationship between budgets and cybersecurity.
General consensus has it that bigger budgets equate to better security, but undoubtedly the security analysts at Desjardins Group would beg to differ. The Canadian lender revealed that it had spent $70 million CAD on its security operations prior to an attack that ended up exposing the personal data of 2.9 million of its members.
A report conducted by the Ponemon Institute confirmed the upward path in the cost of a data breach, that in 2020 was at $3.86 million. While the impact of suffering from a cyber-attack remains high for all companies, irrespective of how big they are, where they are or what they do, the report did confirm that companies can exert some control in managing the cost of a data breach.
Interestingly, the study found that while there has been a 10% rise in cybersecurity costs over the last five years, 2019 saw a decrease in costs by 1.5%. The researchers attributed this decrease to companies who had taken effective precautions and processes, which contributed to coming out of 2020 relatively unscathed, and yet still in budget.
The Costs of a Data Breach that can be Controlled
Depending on the configuration of a SOC, there are numerous aspects where the costs can be kept under control with the right combination of technological capabilities and processes.
- Time Managing Endpoint Protection
This cost is born out of inordinate management overhead due to the use of multiple endpoint products, burdensome maintenance work, constant updates, and patching required. SOC teams should seek out cybersecurity solutions that have wide platform play and provide protection across different devices, OS, and environments. They should require only the occasional update (ideally, just once or twice a year). This relieves SecOps employees of many of these manual and mundane processes.
- Time Investigating Endpoint Threats
This includes costs associated with the manual investigation of alerts and addressing false positives. Activities redressing alerts that are ultimately found to be benign, conducting triages and threat hunting activities contribute to a significant consumption in security analysts’ time. To address this security analysts should be using solutions that provide a high degree of detection accuracy (best-in-breed is a 99% and a 0.1% false-positive rate). Also, when considering a new vendor solution, it’s worthwhile to check what manual processes are automated and the degree to which threat analysis is provided in bite size actionable slices.
- Time Remediating Endpoint Attacks
This cost includes all the activities undertaken by security engineers in remediating endpoint attacks, such as restoring from back-ups, re-imaging machines, and so on. The coronavirus pandemic upscaled the risk profile of endpoint attacks, not only due to the increase in attempted attacks but also due to added difficulties of remediating attacks on a remote workforce. As the perimeter no longer really exists anymore, SecOps need to refocus their attention on where events are occurring, and that is on the endpoint.
- Minimizing the financial loss due to user downtime
Endpoint attacks not only create remediation work for an organization’s IT security analysts, but they also impact the productivity of affected employees with the result of causing an organization even further financial loss. With employees working remotely, COVID-19 even further amplified the detrimental impact of an attack. Over the course of the pandemic, average user downtime per endpoint attack went up to 12 hours, as now the affected employee would have to cease work until they were able to obtain a replacement computer and set it up for usage. One of the ways SecOps can minimize the impact of these consequences of being breached is by retiring legacy solutions. Whether it be a legacy EDR or anti-malware software, these solutions simply cannot keep up with the modern threat landscape.
- Minimizing Likelihood of a Material Breach
Weaknesses in vendor products combined with a remotely located workforce that make it difficult to define the norm in user behavior, create loopholes for attackers to gain a foothold within an organization, especially through endpoint devices. By establishing a security operation that is not constantly flooded with alerts and overwhelmed by investigation activities help to close this window of opportunity. Eliminating alert fatigue allows security operations to pounce on the fewer threats that may manage to still get through.
Beyond these costs, there are also harder to quantify sources of financial loss to business operations. The non-direct impact of a security breach can include brand reputation damage, customer attrition, regulatory fines, customer reacquisition costs, and compensation payouts.
Avoiding a Budgetary Journey to Bust
Despite the multiple moving parts that contribute to the cost-efficiency of a cybersecurity operation, with the right combination of technology, automation and optimal processes, the cost of securing an organization can be brought down. A Forrester Total Economic Impact Study found that customers of Deep Instinct were able to reduce their costs by 446%. The study which compiled the responses of customers into a representative organization of 7,000 endpoints managed by a SecOps team of 15 employees, calculated that they were able to reduce security operation costs by $3.5 million.
A break-down of the cost savings for each of the elements listed above can be found here:
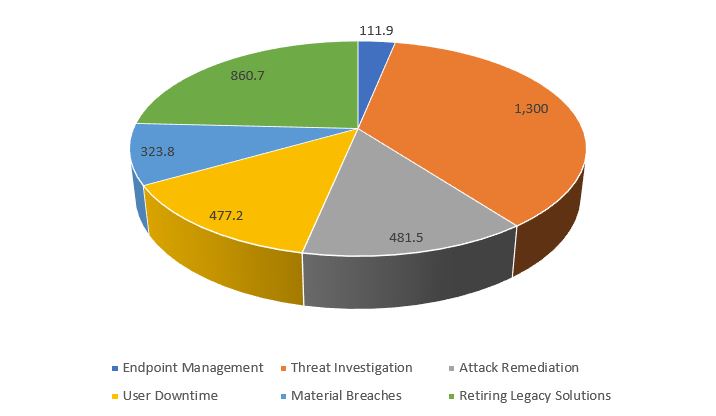
Figures are indicated in terms of thousands of dollars. The biggest cost saving was $1,300 million in time saved in threat investigation work, retiring legacy solutions was another big cost-saver at $860.7K.
Through the investment in Deep Instinct, the interviewed customers reported both quantitative and qualitative benefits against the backdrop of enhanced endpoint security. The early prevention through deep-learning predictive algorithms meant that the representative organization was able to prevent more attacks from occurring pre-emptively, they were able to get better visibility and control over the far fewer attacks that still managed to slip through, and SecOps employees were able to reallocate their time towards higher-value tasks and projects. The implementation of Deep Instinct reduced the number of false positives by 99% and significantly alleviated the workload placed on SecOps.
To learn more about how these customers were able to optimize their cybersecurity environment and put their budgetary figures in the green, we recommend checking out the full Deep Instinct TEI Study.






