Meet MyloBot - A New Highly Sophisticated Never-Seen-Before Botnet That's Out In The Wild
Over the past few years, we have seen various ways of spreading malicious code, one main infrastructure of spreading malware being the dark web.
Lately, we have noticed a highly complicated botnet (number of internet-connected devices, where the owner can control them using command and control servers), which was detected and prevented in one of our client’s live environment and devices - by our deep learning cybersecurity solution. This botnet presents three different layers of evasion techniques, including usage of command and control servers to download the final payload. the combination and complexity of these techniques were never seen in the wild before.
Botnets can theoretically perform anything – depending on the payload. The payload can vary from DDoS attacks, steal data, and even installation ransomware which can cause tremendous damage.
What it does
This highly sophisticated botnet incorporates different malicious techniques:
- Anti VM techniques
- Anti-sandbox techniques
- Anti-debugging techniques
- Wrapping internal parts with an encrypted resource file
- Code injection
- Process hollowing - a technique where an attacker creates a new process in a suspended state, and replaces its image with the one that is to be hidden
- Reflective EXE - executing EXE files directly from memory, without having them on disk. This kind of reflection is not very common and was first published by Deep Instinct in Blackhat USA 2016
- It also has a delaying mechanism of 14 days before accessing its command and control servers.
The fact that everything takes place in memory (while executing the main business logic of the botnet in an external process using code injection) makes it even harder to detect and trace.
When we traced the command and control server we revealed that it was used by other malware campaigns as well which originated from the dark web.
The dark web plays a critical part in the spread of malware: Its rather simple accessibility of services and knowledge has made it easy for any attacker to gain much more abilities in minimum effort. The first example for this, is the shared knowledge in forums: in the dark web, attackers trade methods and techniques in underground forums, thus exposing knowledge to additional malware developers.
Another example, which has increased in the past couple of years, is the amount of malware for sale on dark web markets. By using the dark web, anyone today can access an online market and purchase a malware. Prices vary, from simple malware that costs several dollars to malware sold at hundreds of dollars as “fully undetectable”. Other than the malware itself, malware developers can purchase services that assist in the infection process. An attacker can purchase access to exploit kits, buy traffic of tens of thousands of users to a web page, or even buy a full ransomware-as-a-service for his own use.
Malware vs. Malware
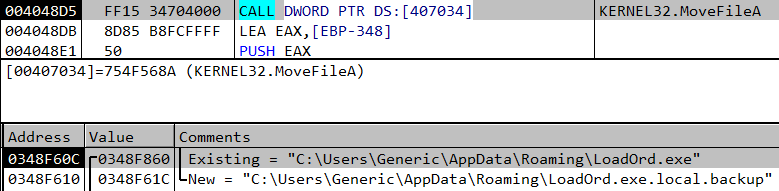
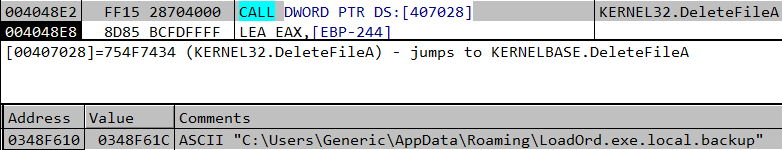
Part of this malware process is terminating and deleting instances of other malware. It checks for known folders that malware “lives” in (“Application Data” folder), and if a certain file is running – it immediately terminates it and deletes its file. It even aims for specific folders of other botnets such as DorkBot.
We estimate this rare and unique behavior is because of money purposes within the Dark web. Attackers compete against each other to have as many “zombie computers” as possible in order to increase their value when proposing services to other attackers, especially when it comes to spreading infrastructures. The more computers – the more money an attacker can make. This is something we’re seeing here as well.
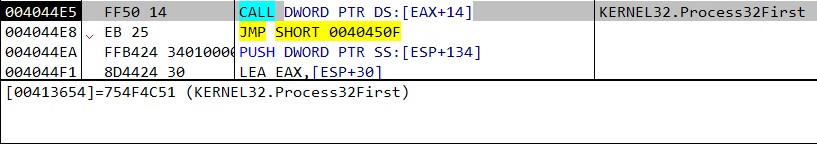
Comparing current running process on the list to a file located in %APPDATA% (“LoadOrd.exe” in this case)
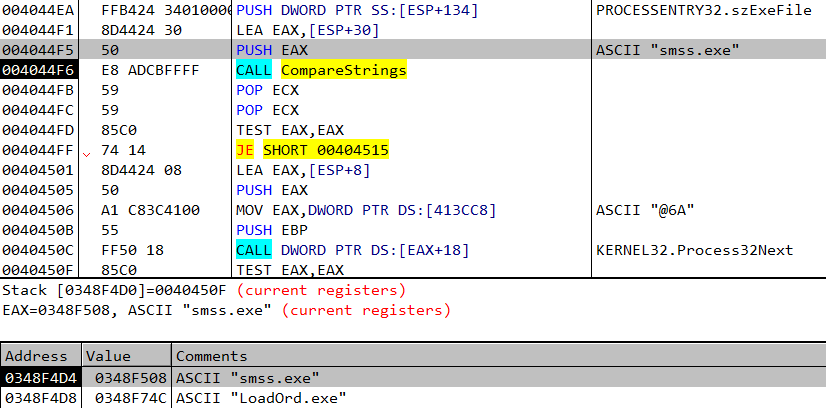
In case there is a match, terminate the process and delete it
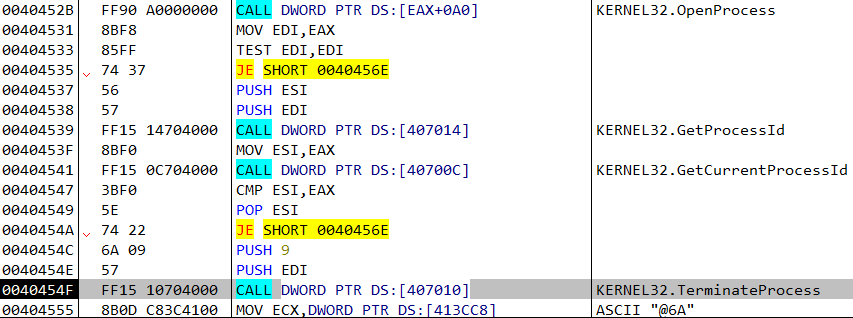
The Expected Damage
Once installed, the botnet shuts down Windows Defender and Windows Update while blocking additional ports on the Firewall. It also shuts down and deletes any EXE file running from %APPDATA% folder, which can cause loss of data. The main functionality of the botnet enables an attacker to take complete control of the user’s system - it behaves as a gate to download additional payloads from the command and control servers. The expected damage here depends on the payload the attacker decides to distribute. It can vary from downloading and executing ransomware and banking trojans, among others. This can result in loss of tremendous amount of data, the need to shut down computers for recovery purposes, which can lead to disasters in enterprises. The fact that the botnet behaves as a gate for additional payloads, puts the enterprise in risk for leak of sensitive data as well, following the risk of keyloggers / banking trojans installations.
Although this kind of complexity in the malware’s structure is extremely rare, Deep Instinct detected and prevented it on a client’s production environment. Once again, this is a true testament for the superiority of deep learning based solutions in the cybersecurity warfare.
For a full detailed analysis of Mylobot, download our free research paper on botnets>>