The Evolution of Ransomware and its Culmination to the Name&Shame Game
There has been a shift in the threat landscape when it comes to ransomware and it’s a very worrying trend! Before, ransomware was designed to be a quick payday post-ransom of an environment, but it has morphed into something completely different, becoming an enterprise of its own.
Let’s briefly talk about the history of ransomware, where it started and where it is heading. The first major incident pertaining to ransomware surrounded the “PC Cyborg” or AIDS trojan. The ransomware would lie dormant on the machine until certain conditions were met and then launch, demanding payment and a software license fee. One of the first PC Cyborg/AIDS trojan events occurred in 1989 when a researcher sent out countless disks to “fellows” and unwittingly unleashed the start of a completely new wave of cyberattacks against organizations.
For brevity, let’s jump ahead in this brief history of ransomware to the more “recent” evolutions which have become relatively prominent and for which this writer has direct experience. Starting in 2013 ransomware became substantially more prominent in enterprise environments. Prior to that most of what was encountered was “Fake AV” or other pop-ups trying to get you to pay money to “clean your system”, but they did not encrypt it and leave it unusable.
Early 2013, Cryptolocker and Cryptowall made their appearances featuring sophisticated methods to get around endpoint solutions and encrypt the machines. If successful, this forced the victim to either restore from a backup or pay the ransom to “restore” their data. Countless people fell victim to these new ransomware tactics, to the extent that these new variants of ransomware got labeled “the worst ever”. There were many different variants of Cryptowall and Cryptolocker, as it was constantly updated with better encryption and evasion techniques to avoid sandboxing and endpoint security solutions. Most of these involved utilization of svchost.exe for process injection combined with a command and control server used to provide part of the encryption key.
Just as endpoint security has evolved to keep ahead of bad actors, bad actors have likewise evolved their skills to circumvent detection. The more successful efforts going one step further to incorporate new techniques to ensure they receive payment. Mentioned earlier were command and control servers, this was the bread and butter of the early ransomware wave and it made circumvention of the endpoint security extremely easy. All that was needed was for an innocuous file to get on the machine which could then reach out to download the payload once on the machine and “found clean” by the endpoint solution. Two examples of campaigns that used this level of technology, which was groundbreaking at the time, were GameOver ZeuS/CryptoLocker. This writer personally dealt with all of these in a prior role and can attest to it being a living nightmare. The bad actors were clearly very aware of the security measures being used on the field and knew precisely how to counter and exploit them.
Eventually, it was found that having a C2C (our short form for command and control) server in the environment was extremely dangerous as it required the machine to reach out and download the file. The persistent server(s) was a weak point that could be tracked, and in the case of CryptoLocker/CryptoWall it led to their downfall. A large factor in this takedown was the need for a persistent file on the machine to talk back to the C2C server. Ultimately this allowed for endpoint security solutions to obtain a copy of the file and reverse engineer the inner workings which revealed the servers they were talking to.
Once these servers started getting taken offline and the “admins” who were overseeing them arrested and tried for their crimes, a shift started to take place. Instead of hosting the files on a C2C server that was able to be tracked, bad actors started using sites like PasteBin to house their binary payloads. Now, all that bad actors had to do was drop a simple batch file on a machine and have it call back. The more intelligent ones (Sodinokibi, Ryuk, etc.) were injecting straight to memory once the PasteBin site was accessed and thus circumvented almost every endpoint solution. Even worse, many MSPs were encrypted using their own RMM utilities, something which is still happening today, with the most recent trend in the threat landscape to name and shame.
In the new transition to “name and shame” just ransoming the data is not enough to ensure the payment, so the bad actors implemented a new tactic to secure their payday. The same premise is at play with the attacks in the sense of encrypting the data and leaving a ransom note, but that is where the differences start to take shape.
Here is an example of the ransom note:
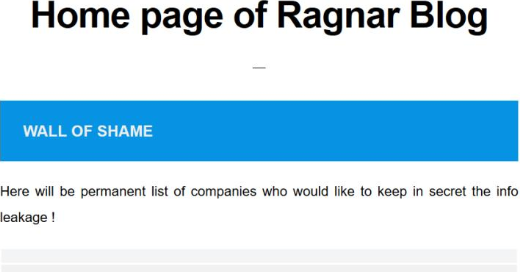
There is a website on the dark web which houses any and all companies which are breached by Ragnar Locker and either decided not to pay or never responded to the notification file because they felt it was an idle threat.
And this is where this ransomware starts to differ from its predecessors. On line 23 you see they make the ultimatum of “you will contact us, or we will publish this for sale to interested parties”. This differs from ransomware in the past which encrypted your files, but you were free to restore from backup without any threat of anyone knowing the data breach ever happened. While many out there are thinking “oh, this is just an idle threat in an attempt to extort money from a company”, that’s now wishful thinking and no longer viable.
Line 26 then addresses the gathering of sensitive information from the company. This too sounds like a generic idle threat designed to force the victim into a panic decision to pay “just in case it’s real”.
Line 27 states all files and documents will be published for all to see. On top of that, they will reach out to the companies they found in the documents with direct links to let them know their data was exfiltrated and the security of the company was compromised.
Look at the next picture and try not to become overwhelmed with dread and worry. This is a screenshot of the internal file structure of the data pulled from servers by a company which was encrypted by Ragnar Locker.
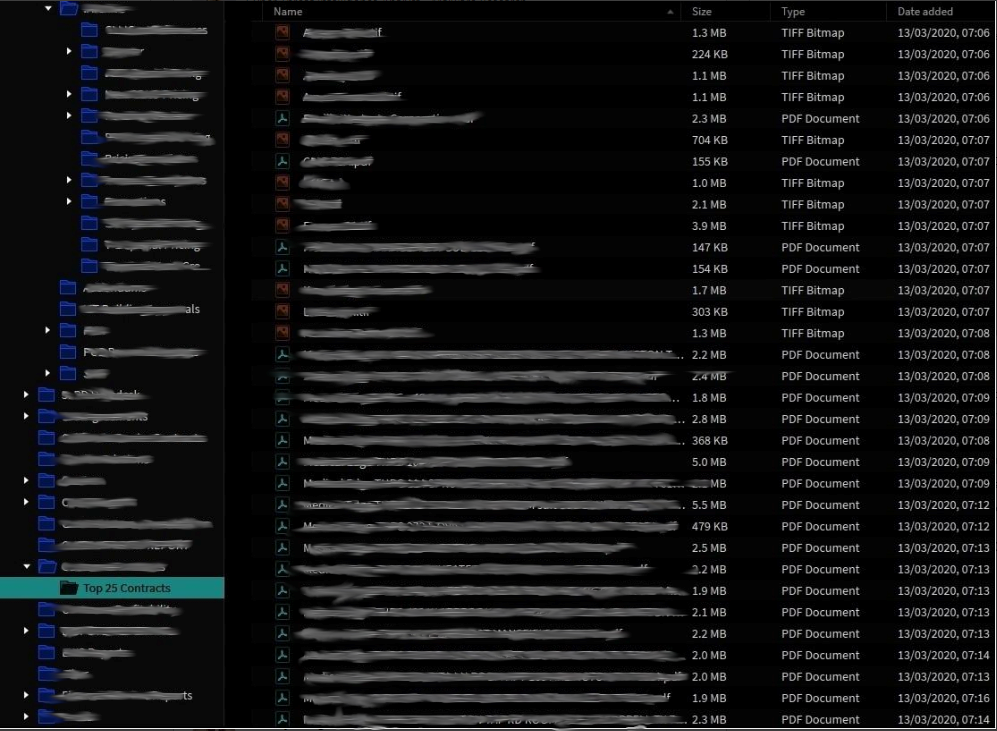
I have blanked out the data, which was wide open, very enlightening, and sadly out there for the whole world to see! It included company names and even addresses as that was the naming convention for the documents as they were pulled from the environment. As you can see, they are not passing you an idle threat but should be taken seriously.
What happens if you don’t pay? How severe can it get? Take a look at the next image.

They have listed the name of the company and the website in their release. They also go to the extreme of listing the head of the company to add a bit more insult to the injury of data being readily available for purchase by any and all parties. Leaving companies minimal alternative but to follow the negotiations with the Ragnar team.
Yes, these guys mean business but that doesn’t mean the whole situation is lost. It is possible to keep yourself protected against them by having a next-generation solution designed to prevent such attacks. I have run this through my lab to test whether Deep Instinct successfully prevented against Ragnar ransomware. The pictures speak for themselves!

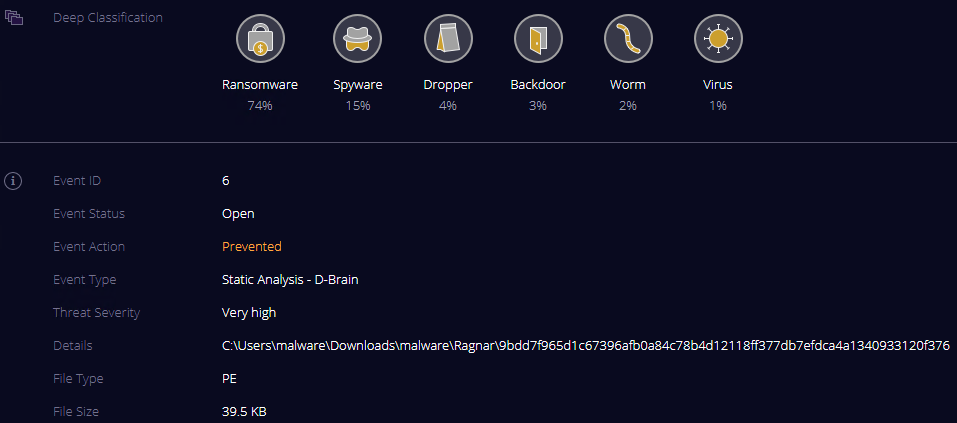
This is a breakdown of what was found when Deep Instinct’s deep learning brain analyzed the file as it was being extracted from the zip package on the lab machine. The hash value listed is the IOC which is used in this writer’s lab for testing purposes. (SHA256 IOC - 9bdd7f965d1c67396afb0a84c78b4d12118ff377db7efdca4a1340933120f376) It’s a very small PE file but should it get into your environment you can see the potential damage (both monetarily and to your reputation) it leaves in its wake. The ransom note and the data posted above were from two different attacks, but how did they get in? In the instance of the breach with the note the bad actors used an insecure login to ConnectWise, further vindicating the need for a zero-time model to pair with your zero-trust model that you should already have in place in your environment!
We halted this attack in its tracks, it never even had a chance to get a foothold on one of my lab machines. This is what next-generation prevention looks like and this is what you need in your environment to keep your data safe!
The threat landscape is forever changing, are you ready to evolve with it and embrace the technology needed to protect your environment?

