What’s Hiding in Your Event Logs?
Just when you thought MITRE had identified all attacker TTPs (tactics, techniques, and procedures) something new pops up! Most recently, researchers have discovered a malicious campaign utilizing a never-before-seen technique for quietly planting fileless malware on target machines. This attack hides malicious code in event logs by injecting it into the Windows Key Management Service event logging process (as well as other legitimate processes).
Rise of fileless attacks
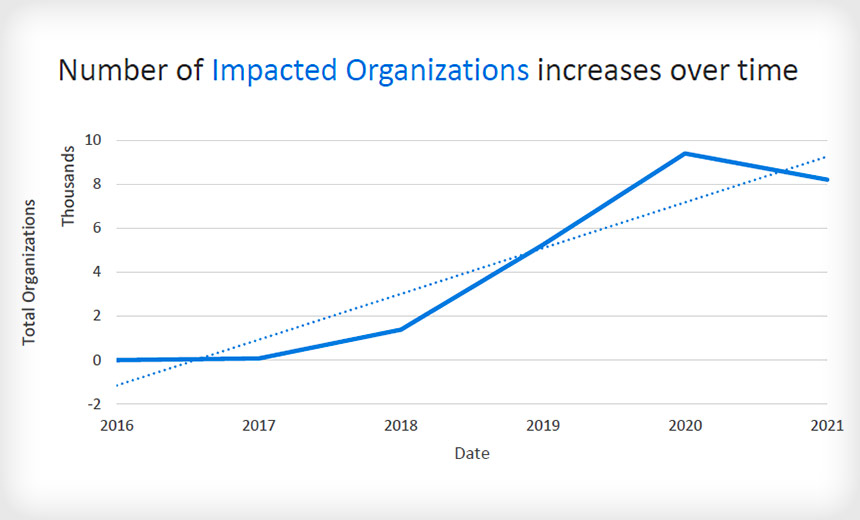
This is yet another example of attackers innovating their attack techniques. In this case, it’s in the form of a fileless attack, an attack method that has become very popular because of its ability to evade exisiting security controls. Figure 1 below explains how prevalent these attacks have become.
How are attackers using event logs to hide fileless malware?
There are three stages that attackers are using to hide fileless malware in Windows Event Logs. We’ll describe each stage in depth below and show why Deep Instinct’s solutions are effective in combatting this new form of fileless attacks.
Stage 1: Drive-by download
While not a new method, drive-by downloads are still an effective technique to deliver malware to an endpoint.
In this particular case, attackers send victims to legitimate websites where they are tricked into downloading a compressed archive of two powerful commercial penetration testing tools, Cobalt Strike and SilentBreak. Each of these tools is armed with AES decryptors that are used to avoid detection. If Cobalt Strike sounds familiar, that’s because it has been used frequently in recent attack campaigns.
Cobalt Strike is a legitimate toolkit for white hat hackers and penetration testers, and because of its ease of use and availability, it’s usage increased by 161% between 2019 and 2020—and continues to rise* (Figure 2).
How does Deep Instinct help?
For this particular phase of the attack, Deep Instinct’s static analysis provides a key protection—correctly identifying and preventing the threats within the archive, even if the payload were modified to avoid identification.
Stage 2: Injecting the shellcode
Once the tools are downloaded to the system, attackers utilize their capabilites to inject code into trusted system processes or applications. In this case, the Windows KMS (Key Management System) logging process is the perfect “trojan horse” because it is both “hiding in plain sight” and not a place threat hunters are accustomed to looking for malicious shellcode. The reason why it’s classified as fileless is that there are no portable executables or document files with macros. This is also why the detection process becomes very sticky for traditional endpoint security platforms as the malicious code is injected into and runs within legitimate system processes. Nothing appears out of the ordinary in the normal operation of the system.
This type of attack also poses a risk for Endpoint Detection and Response (EDR) solutions because it’s written specifically to evade detection. Subsequently, EDR machine learning models must be re-trained to spot this activity and add it to their behavioral analysis engines. This is a human-led process that takes time to implement and requires an update to the core functionality of the security system.
Another concern is that EDRs are well-known for logging high rates of false positives, which means that many organizations put exceptions in place for well-known system processes and directories to avoid blocking legitimate business activity and cut down on help desk overhead.
Deep Instinct’s approach to fileless attacks
Deep Instinct takes a different approach to provide prevention against fileless attacks utilizing our built-in Memory Protection functionality. The self-learning nature of Deep Instinct means that we can predict and prevent never-before-seen attacks. Human intervention is not necessary to update our deep learning brain to protect against new attacker innovation. The end result is immediate, pre-execution prevention of known, unknown, and zero-day threats.
Stage 3: The big pay(load)off
In the final phase of this new fileless attack, attackers are doing what threat actors do: delivering one payload to rule them all.
The payload used in this particular campaign is one of two remote access trojans (RATs) designed to gain complete remote control over the infected system. In addition to using a new technique of hiding malicious code in event logs, the actual code used and elements of the remote access tools do not hold any similarities to past campaigns. This is yet another cause for concern for EPP/EDR solutions because their detection mechanisms are trained to look for code snippets that will tie back to existing campaigns to correctly classify and identify the threat group and take appropriate action early in the process.
More accurate prevention with Deep Instinct
Deep Instinct’s approach does not make decisions based on static-weighted, human-fed data points. The advantage is that the behaviors, code, and tools used in this attack will all be evaluated independent of any external influence. The result is a more accurate decision that can be made in a shorter amount of time to understand the threat and prevent damage.
Fileless Malware finds its match in Deep Learning
Fileless attacks pose a significant threat for security solutions like antivirus and EDR. Signature-based engines and machine learning decision models fall short in detecting unknown, never-before-seen attacks. New attacks can be predicted and prevented with a deep learning-based solution, which is exactly where Deep Instinct comes in. With the only deep learning framework developed for cybersecurity, Deep Instinct takes a multi-layered appraoch to prevent >99% of unknown threats with a <0.1% false positive rate.
For more information on how Deep Instinct can prevent fileless attacks contact us.
Further reading:
- https://www.deepinstinct.com/blog/evading-antivirus-detection-with-inline-hooks
- https://www.deepinstinct.com/blog/do-not-exchange-it-has-a-shell-inside
- https://www.deepinstinct.com/blog/what-makes-powershell-a-challenge-for-cybersecurity-solutions
- https://www.deepinstinct.com/blog/cobalt-strike-post-exploitation-attackers-toolkit
Resources
Attackers Use Event Logs to Hide Fileless Malware
Researchers have discovered a malicious campaign utilizing a never-before-seen technique for quietly planting fileless malware on target machines.
Attackers Increasingly Using Cobalt Strike
Report: Pen Testing Tool a Favorite Among Lower-Level Threat Groups
Fileless Attacks: Addressing Evolving Malware Threats
Unlike traditional malware attacks, fileless malware does not require installing code on software or systems. Fileless payloads are instead used to infect computer memory, using pre-installed system tools to execute a ‘living off the land’ attack.

