The Abuse of Alternate Data Stream Hasn't Disappeared
The following blog post presents the concept of Alternate Data Stream and how it has been used in the wild, in the past as well as these days: as a technique used to hide a malicious payload in the file system. Although it might be considered an old technique, it is still relevant today and common in the wild.
What is an Alternate Data Stream?
Alternate Data Stream (ADS) is the ability of an NTFS file system (the main file system format in Windows) to store different streams of data, in addition to the default stream which is normally used for a file. When this feature was created, its main purpose was to provide support to the macOS Hierarchical File System (HFS).
The NTFS file system contains files with attributes. The relevant attribute for our scope is the $DATA attribute, which is used to store the data streams of a file.
In the past, it was common to store a malicious payload within an ADS of a legitimate file. But today, many security solutions will detect and scan ADSs’. However, we will show you in this post, an ADS can still be used to run payloads while being hidden from the user as well as various security products.
To simplify the concepts that are presented in this article, all the examples are based on native tools in Windows.
How to Use ADS
In the good old days of Windows Vista, Alternate Data Streams (ADS) was a common method for malware developers to hide their malicious code. An alternate Data Stream was effectively used to his the presence of malicious corrupting files, by squeezing it inside a legitimate file. By putting malware in the Alternate Data Stream, the Windows file would contain information and directions for the legitimate files, but also for the malicious file. In order to run the malicious code the hacker has deposited in the Alternate Data Stream, s/he would want to create a symlink using the mklink command. But doing this necessitates having administrative rights on the machine. Considering the normal behavior of a user doesn’t require running operating as an admin, hackers tend to approach their targets assuming that they land on a box without any admin rights.
Enumeration - The mainstream under $DATA is the empty string (thus: “”, also called the unnamed stream). This stream is used to contain the regular stream of a file.
The following is an example of enumerating the data streams of a file with PowerShell:

You can also use dir /R, or SysInternals\streams.exe to enumerate an ADS of a file / recursively on a directory
As you can see above, the file only contains the unnamed stream.
However, sometimes you can find an ADS within a legitimate file, as there are several legitimate uses for this technique.
Below is an example of enumerating data streams of a file with an ADS with PowerShell:
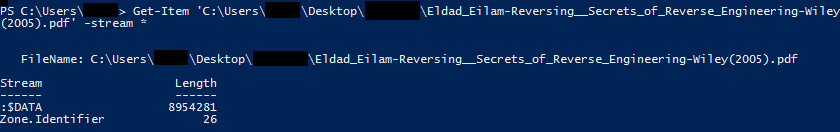
This is also an example of a legitimate use of ADS: the Zone. Identifier. This field presents the trust level of the file’s source. This is a browsers’ usage to store the Its macOS corresponding is the “quarantine bit”.
Creation - While there can be legitimate uses for ADS, ADS can also be used to store a malicious payload. Attackers might prefer this method over saving the payload in the unnamed stream, because its presence will be hidden from the user – it is not accessible from explorer.exe (and the displayed size of a file does not include ADS’s size). In addition, it is not displayed by default with the “dir” command (however, /R flag displays ADS, and is applied from Windows Vista).
Creating an ADS is quite simple.
An example of creating an ADS with type command:
![]()
Until Windows XP, it was possible to run an ADS with the start command. However, since later versions of Windows, it is no longer possible.
Data Access - Abusing ADS is still a relevant threat, as there are multiple ways to read and execute an ADS.
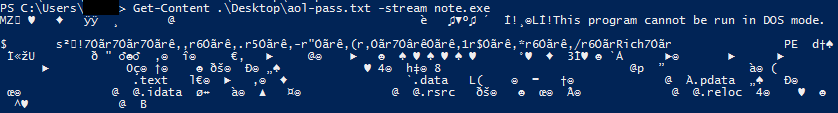
The first usage is accessing the data. The content of the ADS can be accessed easily. The following is an example with PowerShell:
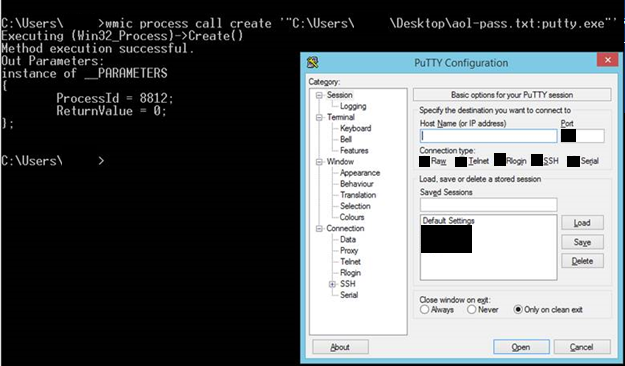
Execution - In addition to reading the data, it is also possible to execute it. Although it’s not possible to execute an ADS with “start” command, it can still be run from other programs. For example, with WMI:
“wmic process call creates” – runs a process with WMI. It can also run an ADS. Example:
There are additional legitimate native tools of Windows that can be used to directly run an ADS. For example, a DLL can be saved inside an ADS and called by DllMain through rundll32.exe; also, an HTA can be saved inside an ADS and called through mshta.exe; and so on.
Malicious Campaigns Abusing ADS
It may seem that Windows has managed to handle the threats that reside within ADS. However, there are many malware families in the wild that still abuse ADS’s.
Another example from 2017 is BitPaymer, ransomware which used two ADS’s in the attack sequence, in order to add stealth to the actions and hide malicious activity. The first ADS was created in order to run the “net view” command to obtain network shares, then the second ADS scrambles the data on the disk and network shares.
To conclude, abusing ADS is a technique that is still relevant nowadays. Indeed, recent Windows versions have limited and hardened the functionality of ADS. However, basic command of native Windows tools such as Power-Shell and WMI, or some knowledge of Windows command-line allows threat actors to continue and leverage ADS in their attacks. Interestingly, recent campaigns using ADS are considered rather sophisticated and tend to minimize the use of persistent files on disk.


