Unfolding the Follina Zero-Day Vulnerability
Zero-day vulnerabilities are among the most difficult threats to guard against because they are – by their very nature – unknown and unseen by threat researchers and most security tools. When these vulnerabilities are exploited, it is a race against the clock to identify them and plug the holes through which threat actors can launch attacks.
What is the Follina vulnerability?
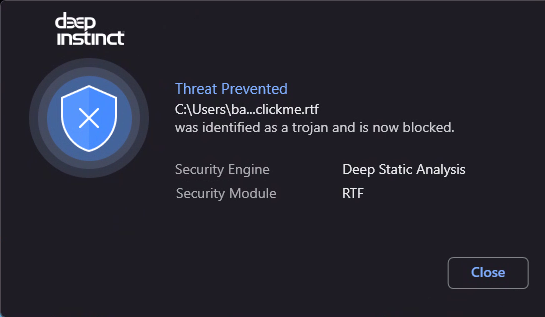
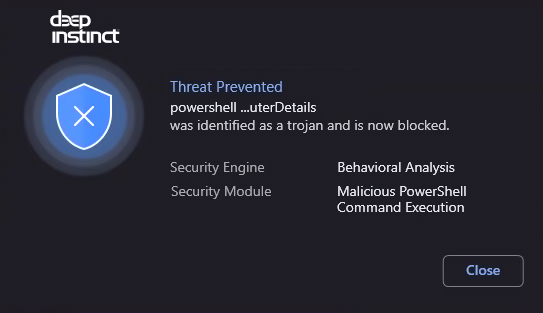
On May 27, 2022, the cybersecurity community became aware of a new zero-day vulnerability in Microsoft Support Diagnostic Tool (MSDT) dubbed “Follina,” which was later given the CVE identifier “CVE-2022-30190.” Follina stems from a bug in MSDT that allows code execution. Under specific circumstances, an attacker can run PowerShell commands on a victim’s machine using a crafty Microsoft Office document or Rich Text Format (RTF) file.
In this post, we will go into a detailed explanation of the exploit, discuss the consequences of an attack, and provide counsel on how your organization can decrease the likelihood of falling victim to a Follina attack.
Follina and the Microsoft Diagnostic Tool
To understand this exploit, we must first understand the issue in MSDT. Normally, when MSDT is called, it asks for a passkey provided by a support professional to continue to the troubleshooting stage.
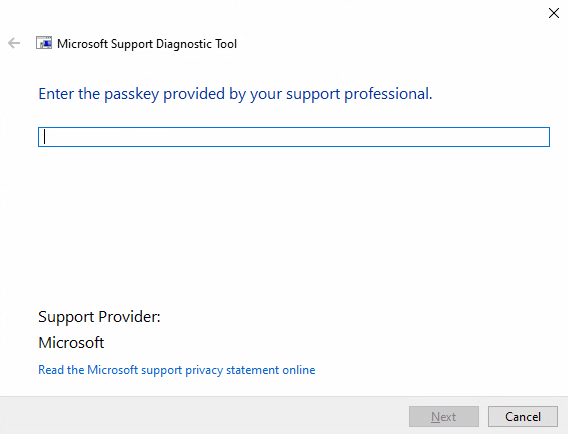
This should provide some level of security and limit access to the troubleshooting utility’s functionality. However, under certain conditions and using a specific syntax, it is possible to execute PowerShell commands via MSDT without providing a passkey.
The Follina exploit
To leverage this bug, an attacker can create an HTML file that calls the troubleshooting wizard using “ms-msdt” and forces it to execute PowerShell code by adding specific parameters to its command, like in the following example:
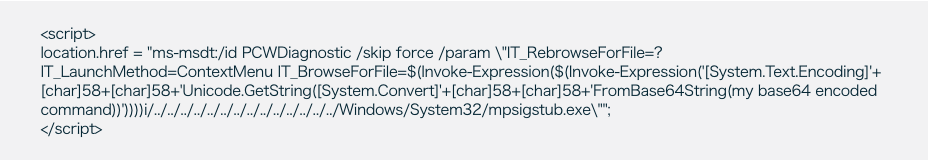
This method can also be used to execute a binary:
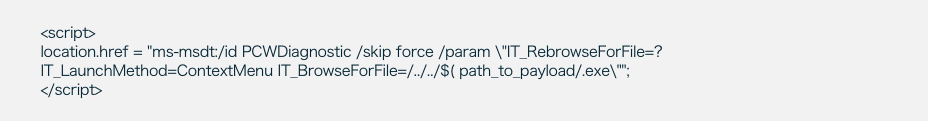
This method allows an attacker to do anything from execute ransomware to open a reverse shell, from which they can run unlimited commands on a victim’s machine. The possibilities available in this scenario are virtually limitless.
However, this will only work if the HTML file’s size is at least 4096 bytes, something that can be easily achieved by adding hefty comments to the file.
How do attackers use Microsoft to deliver Follina?
Attackers do not simply cross their fingers and idly hope someone will land on the address in which their malicious HTML file is hosted. They lure victims into their trap – and this is where Microsoft Office documents and RTF files come into play.
As explained in this blog, by modifying the relationship file (RELS) of a Microsoft Office Open XML (OOXML) file, a threat actor can cause the Microsoft Office document to open an HTML file hosted on the internet and execute a script if it contains one, without it being visible to the user. With a document like this in hand, the attacker can simply send the file to unsuspected users – for example as an email attachment – and persuade them to click it. Once this action is performed, MSDT will be called, and the malicious actor’s command will be executed.
Moreover, if the attacker chooses an RTF file instead of a Microsoft Office document as their initial point of access, things can get even scarier. In this scenario, the infection can occur even if a user just hovers over the file – they do not need to even open the file in order for the wheels to start rolling.
How is Follina executed?
Even though the code that runs via MSDT will probably not be visible to the users, attackers cannot hide the execution of the troubleshooter itself.
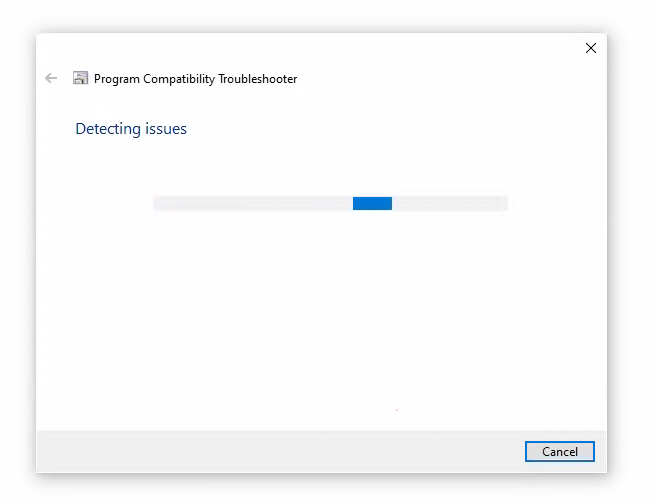
When “ms-msdt” is called, a troubleshooting wizard window will appear, informing users that it is working on detecting issues. Of course, this does NOT alert users that the real issue they should be concerned about is the malware that is currently running on their computer.
To those unfamiliar with Follina, this can be seen as relatively harmless, especially if they have encountered similar troubleshooters in the past. However, to someone who has heard of Follina, this should raise an immediate red flag.
Deep Instinct zero-day detection and prevention
At the time of this writing, Microsoft has not issued a patch for “CVE-2022-30190” and only advised users to disable the MSDT URL protocol.
Deep Instinct prevents Follina and other zero-day threats, pre-execution. Using deep learning models to prevent malicious files from being executed, Deep Instinct can predict and prevent known, unknown, and zero-day threats in <20 milliseconds, 750X faster than the fastest ransomware can encrypt. Our deep learning, prevention-first approach allows us to detect and prevent even the most advanced threats with >99% zero-day accuracy.
If you’d like to learn more about our malware, ransomware, and zero-day prevention capabilities – including our industry-best $3M no-ransomware guarantee – we’d be delighted to give you a demo.