A Jar of Malware
JAR (Java Archive) is a cross-platform file format based on the ZIP format, which can be used in Windows, Mac OSX, Linux, Android OS and more. Its goal is to provide developers the option to compress all their project components (Class files, sounds, and images) into one archive. JAR files can be executed with the command ‘java -jar <jar_file>’. In Windows, they can even be executed with a double click.
For a file of this format to run, the Java Runtime Environment (JRE) needs to be installed. Since this requirement may not be met on an average computer- many malware authors choose not to use this file format, but those who do, can enjoy the cross-platform features that Java has to offer- with just a single piece of malware, attackers can infect multiple endpoints running different operating systems. Moreover, since this attack surface is sometimes ignored by the security software, malicious JAR files may have lower chances of being detected than their executable counterparts.
JAR Malware’s History of Havoc
One of the oldest examples of JAR malware is ‘Red Browser’, the first trojan designed for cell phones running J2ME (Java 2 Mobile Edition). The malware, which appeared in early 2006, presented itself as a platform for sending SMS messages free of charge to induce users to let it send SMS messages on their behalf. Once the user permission is granted the malware’s goal can be achieved, to send SMS messages to a premium-rate Russian number. This action, which costs the user between five to six USD per message, could not be executed by ‘Red Browser’ in most newer cell phones since they don’t use J2Me.
The most prominent JAR malware, that has been around since January 2013 is ‘Adwind’. This RAT (Remote Access Trojan) takes advantage of JAR’s cross-platform features, and can be executed on Windows, Mac OSX, Linux and since August 2013- Android OS. ‘Adwind’ was developed from the RAT ‘Frutas’. ‘Adwind’ can steal passwords from various internet browsers and Instant Messaging (IM) software. It can also download and run files, steal banking credentials, capture screenshots and more. Through the years, this RAT has been through many changes, including being sold to a different owner and having its name changed more than once, yet despite many revisions, it remained the most prevalent JAR malware. ‘Adwind’ was used in many attacks, including a series of phishing campaigns in late 2015 against large banks in Russia, the United Arab Emirates, Sweden, the United States, and Singapore. To date, this RAT continues to remain active, and in October 2019 a new variant was released. This new version uses many layers of packaging and encryption to avoid detection, along with storing legitimate JAR files amongst malicious ones, loading benign JAR files from its server and using common Java commands.
A different type of JAR malware is ‘ATMJaDi’. As its name suggests, this malware took advantage of Java implementation in a different arena. In spring 2019, the malware was used to attack banks in Mexico and Colombia. The attackers, who most likely had inside information on the ATMs’ functionality, installed their malicious software in a manner that still remains unknown, but is speculated to be achieved through compromising the supply chain or with the use of more inside information. Once the malware reached its destination, it injected itself into the main process controlling the ATM’s actions and thereby got full control over the machine. The percentage of ATMs that use Java in the manner exploited by the attackers is quite small, this combined with the fact that a lot of preparation and practice was probably involved, suggests that the attacks were highly targeted and expected to receive a high remuneration to justify their efforts.
Jars in the Wild
As can be seen in the graph below, the number of JAR malware in recent years has not been consistent, nor do the numbers help to predict what the future holds for this trend. The sudden spike in May 2017, for example, is due to Android ransomware called ‘SLocker’, which resurfaced around this time. The inconsistency of these numbers combined with the fact that even when only a few hundred samples of JAR malware are introduced to the wild, coming across just one of them is be very unpleasant. Therefore, it’s important to ensure that your organization is not left vulnerable to this kind of attack.
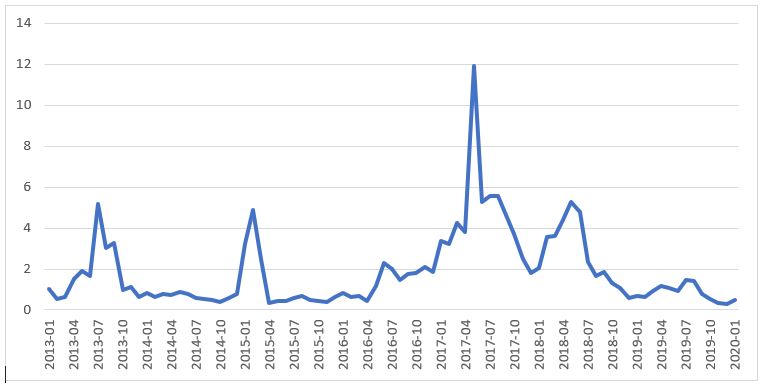
The number of new JAR malware samples in every month between January 2013 and January 2020, shown in arbitrary units.
Keep a Lid on It
Although JAR malware is not a very common attack vector, it cannot be ignored. The cross-platform applicability of JAR malware can enable attackers to infiltrate organizations in multiple areas, with just a single piece of malware. In addition, the fact that this attack vector is less known might enable threat actors to bypass security solutions. As malware authors improve their tactics and add more tools to their arsenal, enterprise security experts should likewise be looking to expand their defense across as many possible surfaces. Due to the imperative of the need to address this threat type, JAR malware protection is an important feature within Deep Instinct’s most recent product version. Deep Instinct is the only cybersecurity company that can detect and prevent JAR malware pre-execution, using our patented deep learning model that was trained to identify malicious Java applications.
Find out more about how malicious JAR files can be prevented before they can cause any damage.

