Deep Dive: Exposing Stealthy New BlackSuit Ransomware
Five weeks ago, the KADOKAWA corporation began to experience service outages affecting multiple websites. The outages spread to other operations and were identified as a ransomware attack by the BlackSuit ransomware group. BlackSuit claimed responsibility and threatened the public release of stolen information on July 1st unless their ransom demands were met.
BlackSuit's ransomware is very similar to the Royal ransomware strain, which itself is considered the successor to the notorious Conti group. This suggests potential connections or shared developers. This connection can be explained in more detail in some of our older material that has been published on the subject: we examined both Conti and BlackBasta, a Conti offshoot.
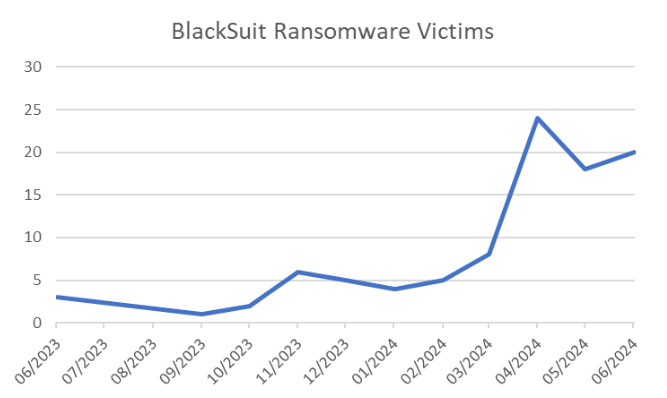
Based on our analysis, we found that Deep Instinct prevents all new Blacksuit Windows Ransomware samples with an eight-month-old brain. Across the industry, however, these samples have a much lower detection rate than earlier sample versions of BlackSuit. As demonstrated in the graph above, that lower detection rate matches the sudden growth of BlackSuit ransomware victims.
The samples BlackSuit is using are well designed for infiltration of legacy systems. Let’s take a closer look.
Latest samples analysis:
Newer samples of BlackSuit’s code mainly added additional layers of complications like encoding strings and imported DLLs for Anti-Analysis. They also added a mandatory ID argument to bypass automatic emulation, making the new samples more evasive.
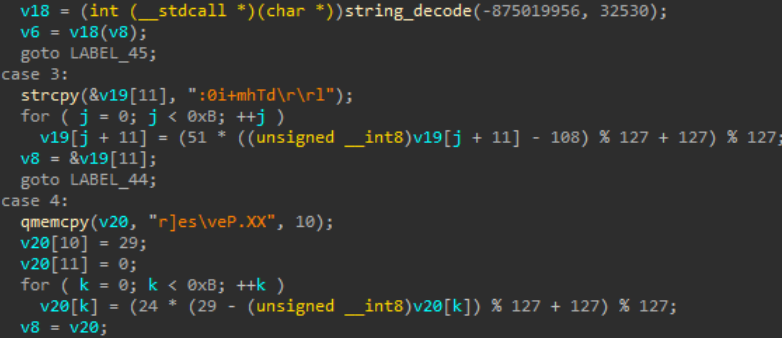
For example, according to VirusTotal, even though old Blacksuit samples have a high detection rate, the new samples from recent months have a much lower detection rate, indicating significant changes.
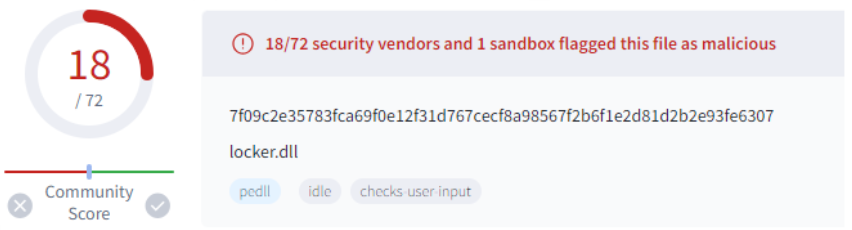
One of the more impactful changes allowed the threat actor to mask the ransomware as a legitimate part of a known free antivirus, Qihoo 360, including false watermarking. This masking has drastically lowered detection. The ransomware is hidden deep inside the legitimate looking application and only has to be executed with a token in the command line to operate as a ransomware.
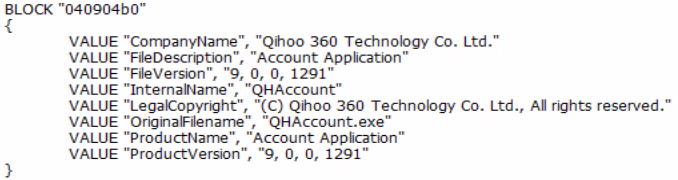
The masquerade file is not signed, indicating this is not the real Qihoo application. The functionality post infiltration remained the same as the other new samples, including the same mutex used.
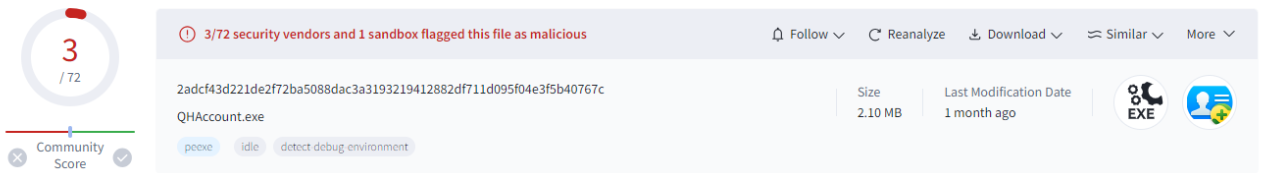
Execution
In the video below, a member of the Deep Instinct Threat Lab Team executes a sample and showcases BlackSuit behavior.
The main portion of the executable is nearly identical to Qihoo's real QHAccount.exe file, resulting in security software evasion.
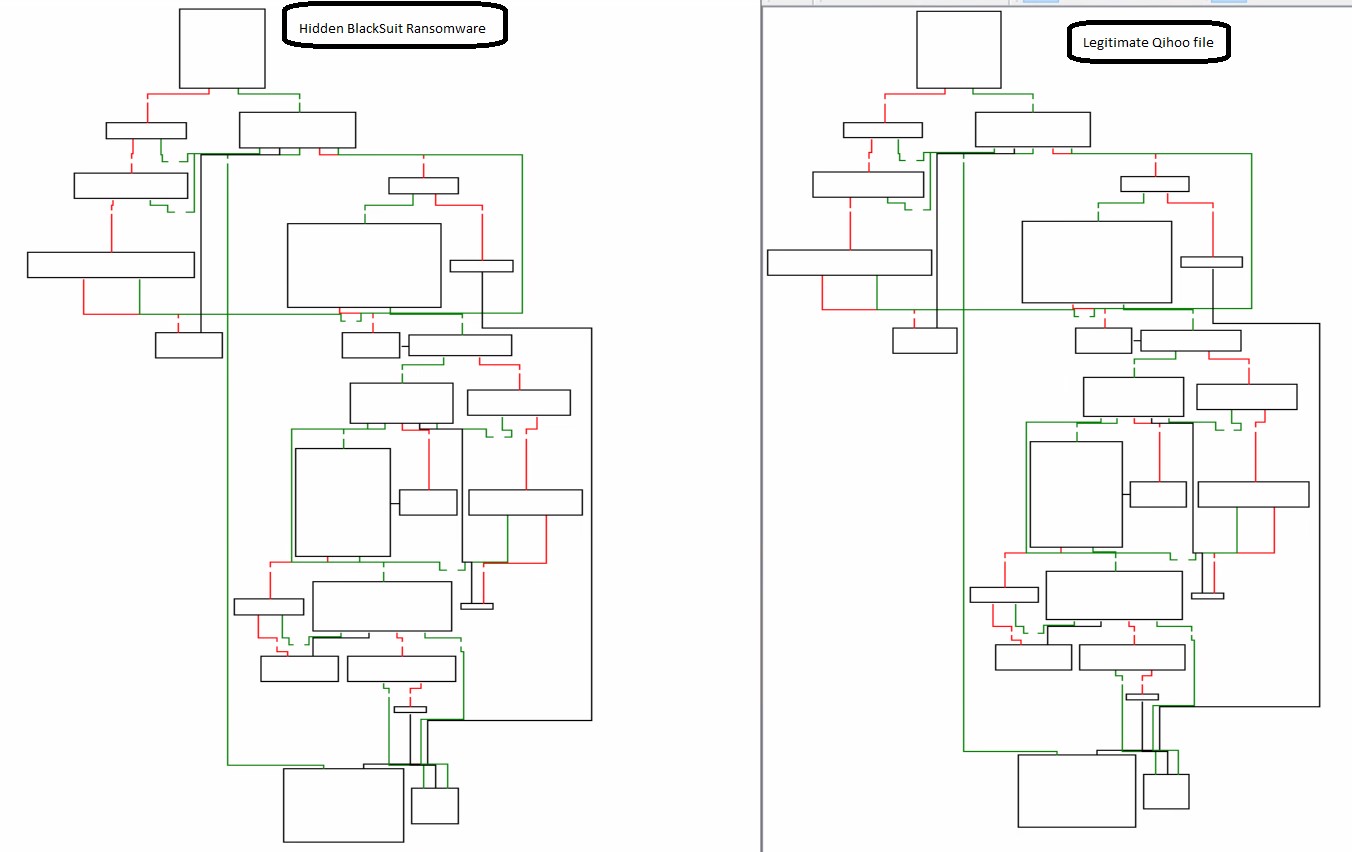
Disclaimer: The official Qihoo 360 is not in any way involved with BlackSuit. The masking is the work of bad actors assuming Qihoo’s identity.
Behaviors:
The common behavior shared with all Windows samples didn’t change much and the main functionality remained the same, though some commands have changed:
-p | Specifies the target directory where the ransomware will encrypt files |
-killvm | Terminates the virtual machine (VM), preventing analysis |
-allfilesEncrypt | Encrypts all accessible files, maximizing damage |
-networkEncrypt | Encrypts files on connected network drives, spreading the attack |
-localEncrypt | Restricts encryption to the local machine storage, limiting immediate impact |
-percentEncrypt | Encrypts a specified percentage of files, potentially increasing performance |
-demonoff | Operates in stealth mode, making detection harder |
-list {file} | A targeted list of files to be included in the encryption process |
-delete | The ransomware deletes itself after execution, hindering investigation |
-thrcount {number} | Specifies the number of threads used for encryption, impacting both performance and resource usage. |
-skip {file} | A list of files to be excluded from encryption |
-noprotect | Disables self-protection mechanisms, allowing termination of the ransomware |
The new samples have encoded strings to complicate analysis, and need to be supplied with -id <32 characters>. They can also receive additional instructions, such as:
-ep | (like the previous percentEncrypt) sets a percentage of each file that will be encrypted. Partial encryption |
-path | Specific directory to encrypt |
-localonly | (an addition to the previous networkEncrypt) without network drives |
-networkonly | (an addition to the previous networkEncrypt) without local files |
-aavm | (like the previous allfilesEncrypt) encrypts everything |
BlackSuit ransomware also boasts a few other functionalities:
Initiates Asymmetric Key Exchange to get the secret encryption key.
Deletes shadow copies, in order to disable easy local restore:
- vssadmin delete shadow /all /quiet
Encrypts
Appends .blacksuit to the encrypted files
Skips:
Various file types like executables, drivers, and installers to avoid breaking the system.
Already encrypted files and the ransom note.
Eventually, BlackSuit’s ransomware is capable of disabling safe mode and shutting down the system:
bcdedit /deletevalue {current} safeboot
shutdown /r /t 0
Drops ransom note: Usually named readme.blacksuit.txt. The content text is encrypted to avoid signature detection for the ransom note. The note includes a link for communication with the threat actor for ransom negotiations.
Infection chain
The common initial attack vectors are RDP (possibly with stolen credentials), VPN and firewall vulnerabilities, Office email attachments (Macros), Torrent websites, Malicious ads, and various 3rd-party trojans. And the attackers have also used tools like CobaltStrike, WinRAR, PUTTY, Rclone, Advanced IP Scanner, Mimikatz, and GMER. The variety of attack vectors opens the possibility for infection across a much broader target group, endangering large amounts of data.
Leak and news site
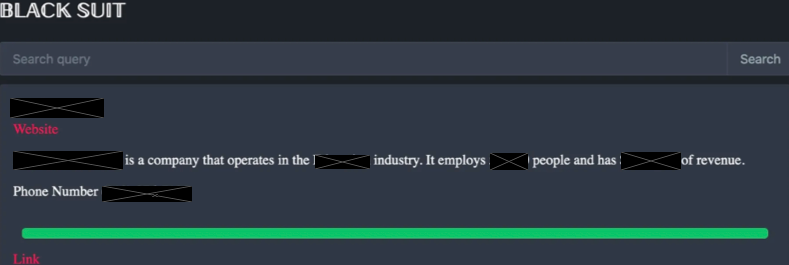
The BlackSuit group operates a news and leak site on the DarkWeb that includes all the known victims of the threat actors. Once the timer for the ransom payment ends, the exfiltrated data is published.
Alleged victims of BlackSuit ransomware have their data published under a profile featuring key information about their organization, including industry, number of employees, revenue, and contact information.
Request a demo to see how Deep Instinct can protect you from BlackSuit ransomware.
Explore the BlackSuit IOCs below.
IOCs
f1684fb118d4d8fc56653fcc49e12a659b64c4459ba037fa94f21783235cc6ba
dede96fd44c0f78eb79ceb63b898874e8922efc59d8bfb9f86505b1992bc00a3
6a2e454942cfeebb1140e1a28cb05fd49461d07792e97663378399c719fbc9ee
79ab73a0e9dd8eac045c00fd1bd172a7f359588901f93c83e6740157eb21e7df
7f09c2e35783fca69f0e12f31d767cecf8a98567f2b6f1e2d81d2b2e93fe6307
60a9785ec20ec08b6792e304fc4b363abd54b8a7a2945dca9f97ee07783c4759
5aeaa5c4f4100b2084814be72a695a5bf4a95fdb8a0c65704523608baa79b726
d96ff4b3e188f7ff96ed28c1381a6318dd76bb1fbd6ca02c6ab0236e1c7f35aa
3be3a3c2c1abc1d401e845a2b8952f4f3e55b510f3d6c1eb2a4503c7be09bec1
90ae0c693f6ffd6dc5bb2d5a5ef078629c3d77f874b2d2ebd9e109d8ca049f2c
6ad8215bd6b52d897dcfa0a9829720d0532adc741460ecb4b8f00c4427b6141c
8605dec4ae4bd9f51297d1f244d0647bc0637d6ce6a957a5f810c64ae63276cb
2adcf43d221de2f72ba5088dac3a3193219412882df711d095f04e3f5b40767c
readme.blacksuit.txt
.blacksuit
vssadmin delete shadows /all /quiet
Mutex: WLm87eV1oNRx6P3E4Cy9


