Top-3 Drawbacks of Content Disarm + Reconstruction (CDR) for Malware Prevention
Application file uploads from external, internal, or third parties are an emerging threat vector.
While traditional approaches like AV and Sandbox have been used by many organizations in an attempt to catch malicious content, they have severe drawbacks when it comes to speed, efficacy, and scale. CDR was created to address these concerns.
On paper, Content Disarm and Reconstruction (CDR) looks quite promising to prevent malicious file uploads. However, it falls short in production.
Below we discuss the history of CDR, its pros and cons, and a better alternative to malware prevention that will significantly reduce risk without friction for the business.

Whitepaper
File Upload Security
Comparison of Single AV, Multi-AV scanning, file sandboxing, and CDR methodologies
Content Disarm & Reconstruction (CDR)
CDR arrived on the scene as a new way of preventing malicious files from entering an environment. Instead of scanning, inspecting, or fully analyzing every file, CDR targets active content within files, such as macros and VBAs, that could be potentially exploited or have malicious intent. The benefit of this technology is that it can work very quickly to inoculate potentially malicious files, so it avoids the delays introduced by file sandboxing.
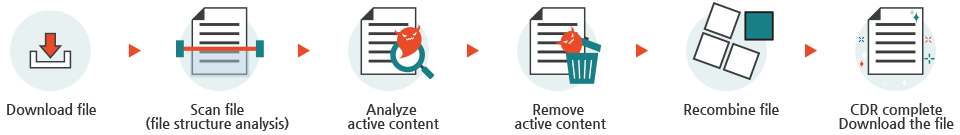
Types of CDR
There are three basic approaches to CDR:
- Flat-file conversion: Takes any new file with active content and creates a flat copy of it in PDF form. While quick and effective at minimizing the attack surface, this method erases legitimate content such as macros, form fields, and hyperlinks, due to its inability to distinguish between malicious and benign files.
- Content stripping: Strips out active content and embedded objects and reconstructs the file in its original format to maintain some usability for the end user. The downside is that, once again, since CDR is unable to distinguish between malicious and benign files, legitimate content is destroyed, and admin interaction is frequently required to retrieve original files.
- Positive selection: Attempts to address the shortcomings of the previous two methods by rebuilding files based on templates which serves to maintain full functionality of the file after reconstruction. It does this by copying only known-good (positively selected) components to the reconstructed file. While this method cuts down on the amount of legitimate content that is removed or destroyed, it is most often inaccurate due to the lack of malware identification capabilities.
Top-3 Drawbacks of CDR for Malware Prevention
In a 2021 report, Gartner states that, “done well, CDR removes all threats from uploaded files without adding significant latency. <sic> The main disadvantage of CDR lies in the fact that it changes the files’ contents.”
Because CDR modifies a file in transit, it has a relatively high probability of delivering a file that cannot be edited or has had significant changes to content such as text and images (see Figure 1). Common issues with CDR-manipulated files include compatibility and font issues that render documents that can no longer be edited, as well as images that are not properly reconstructed or lose their high resolution.
CDR introduces additional work for the IT team in the following ways:
- Since the technology cannot distinguish between legitimate and malicious active content, the CDR tool must examine every file in detail.
- Users who are expecting to receive a spreadsheet with macros from a trusted source will instead receive a flat file with the important functions disabled.
- This in turn necessitates an interaction with a help desk to request the original file.
- In some cases, the original file may not be available by the time the user requests it.
CDR raises some very important business concerns:
- Often, IT must grant exceptions for certain files (or groups) or executive team members who cannot tolerate a delay or a chance that their document will not remain intact.
- In addition, users who know this technology is in place have been known to avoid it and receive their files by different methods, such as a personal email account.
- This negates any benefits the technology may have provided.
CDR only provides protection for a limited amount of file types:
- CDR cannot sanitize portable executable files, such as EXE and DLL, and most image files.
- This creates a wide security gap that must be addressed with a different solution and can also lead to a false sense of security.
A Better Approach: Malware Prevention
As malicious file uploads grow in concern, organizations need a frictionless solution that can prevent malware at a speed and scale that meets the needs of the business. While CDR has some advantages over the traditional methods, we believe the disadvantages far outweigh the benefits.
Deep Instinct Prevention for Applications is a unique malware prevention solution that is implemented without an agent via REST API or ICAP. With the same industry-leading static anti-malware engine that has been proven to prevent threats before they are allowed to execute on the endpoint, Deep Instinct meets the file scanning security requirements for all enterprises with the following:
Fastest Speed
- Makes a malicious vs benign verdict in <20ms for unknown malware
- Delivers decisions autonomously, without a reliance on threat intelligence feeds
Immense Scale
- Scans millions of files per day without latency
- Improves SOC efficiency by reducing false positives to <0.1%
Highest Unknown Threat Efficacy
- Prevents infected Office files and PDFs missed by other solutions
- Stops ransomware before it can open and infect an environment
Utmost Privacy
- Protects data privacy with no data ever leaving a customer’s environment
Stopping unknown and zero-day threats from file uploads is paramount to reducing risk. If you are concerned about file uploads in your environment, it’s time to look at a modern prevention approach to stop the threats before they land inside. To learn more check out the white paper: File Upload Security: The Missing Category for a Comprehensive Security Posture.
Deep Instinct Prevention for Applications was designed specifically to address the need for file upload security, and it does so with unmatched speed (<20ms verdict), efficacy (>99% catch rate), and accuracy (<0.1% false positive ratio), all while maintaining the content and integrity of original files.
To learn more about how you can protect yourself from malicious files anywhere they surface, contact Deep Instinct today.
Resources
- Malicious Office files: 20+ Years of Microsoft Office Exploits
- PDF as a Weapon of Choice on the Cybersecurity Battlefield
- 5 Advantages of Deep Learning in Cybersecurity


%20for%20Malware%20Prevention%20%7C%20Deep%20Instinct&_biz_n=0&rnd=25381&cdn_o=a&_biz_z=1745468591298)
%20for%20Malware%20Prevention%20%7C%20Deep%20Instinct&rnd=113013&cdn_o=a&_biz_z=1745468591302)
